linux下svn伺服器搭建及建立分支
系統環境:Centos 6.5
一 搭建svn伺服器
第一步:通過yum命令安裝svnserve,命令如下:
>yum -y install subversion
此命令會全自動安裝svn伺服器相關服務和依賴,安裝完成會自動停止命令執行
若需檢視svn安裝位置,可以用以下命令:
>rpm -ql subversion
第二步:建立版本庫目錄(此僅為目錄,為後面建立版本庫提供存放位置)
選擇在var路徑下建立版本庫,當前處於根目錄下,一次性建立如下:
>mkdir /var/svn/svnrepos
第三步:建立svn版本庫
在第二步建立的路徑基礎上,建立版本庫,命令如下:
>svnadmin create /var/svn/svnrepos/xxxx (xxxx為你預期的版本庫名稱,可自定義)
建立成功後,進入xxx目錄下
>cd /var/svn/svnrepos/xxxx
進入目錄,可以看見如下檔案資訊:
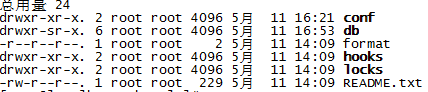
第四步:配置修改
svnserve.conf 檔案, 該檔案配置項分為以下5項:
anon-access: 控制非鑑權使用者訪問版本庫的許可權。
auth-access: 控制鑑權使用者訪問版本庫的許可權。
password-db: 指定使用者名稱口令檔名。
authz-db:指定許可權配置檔名,通過該檔案可以實現以路徑為基礎的訪問控制。
realm:指定版本庫的認證域,即在登入時提示的認證域名稱。若兩個版本庫的認證域相同,建議使用相同的使用者名稱口令資料檔案
2)許可權分配
# vi /home/svnroot/repository/authz.conf
[groups]
admin=useradmin
devteamcs = useradmin,user1,user2//這裡定義了一個使用者組
[/]//對所有的專案,所有的使用者都有讀許可權,admin使用者有讀寫許可權
@admin = rw
* = r
進入已經建立好的版本庫目錄下,也就是前文說建立的xxxx
進入conf
>cd /var/svn/svnrepos/xxxx/conf
conf目錄下,一共存放三份重要的配置檔案,如下:
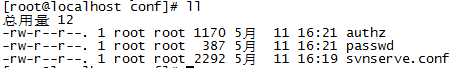
authz:負責賬號許可權的管理,控制賬號是否讀寫許可權
passwd:負責賬號和密碼的使用者名稱單管理
svnserve.conf:svn伺服器配置檔案
細節修改如下:(希望大家嚴格按照以下資訊,不用參考網路上其他資料)
修改authz檔案資訊,如下:
>vi authz
在檔案內容的末尾,新增如下:
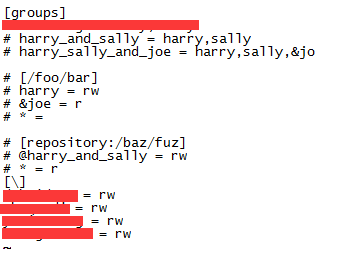
只需在末尾新增,無需在檔案其他部分修改和新增任何東西(請忽略groups被我馬賽克的地方,那其實也是條無用的記錄,我忘記刪掉而已),末尾內容如下:
[\]
賬號1 = rw
賬號2 = rw
。。。。。
rw表示賦予此賬號可讀寫的許可權,請注意[]中的斜槓,一定是反斜槓,有些教程說,需新增版本庫名稱在括號內,我直接建議就這寫,這樣寫允許訪問的許可權更大,避免一些錯誤
修改passwd檔案資訊
>vi passwd
賬號密碼檔案無需做修改,也是直接將賬號和密碼資訊追加到檔案中即可,注意格式為:
賬號 = 密碼
例如:admin = 123456
修改svnserve.conf(重要)
vi svnserve.conf
原始檔案內容,都被註釋掉的,我們只需要去掉4條指定內容前註釋即可,如下:
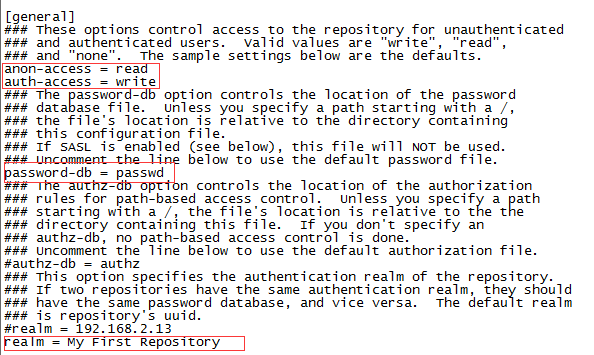
大多數網路資料,都會讓大家將authz-db = authz這條給去掉註釋,經過我本人多次被坑經驗,此條去掉後,雖然svn伺服器可以連線,但一直會提示“認證失敗”,註釋掉即可正常
還有多數資料會讓大家在realm = My First Repository處填寫伺服器ip,經過測試,填寫後並無什麼用處,所以大家去掉註釋即可,無需做任何修改
到此,配置已經全部完成,賬號資訊已經新增成功
第五步:防火牆開啟
多數情況下伺服器安裝完成,配置完成後,無法連線svn伺服器,均是防火牆問題,大家按照如下3條命令逐一執行即可
>/sbin/iptables -I INPUT -p tcp --dport 3690 -j ACCEPT
>/etc/init.d/iptables save
>service iptables restart
執行結果如下圖:
Centos 7 firewall 命令:
檢視已經開放的埠:
firewall-cmd --list-ports- 1
開啟埠
firewall-cmd --zone=public --add-port=80/tcp --permanent- 1
命令含義:
–zone #作用域
–add-port=80/tcp #新增埠,格式為:埠/通訊協議
–permanent #永久生效,沒有此引數重啟後失效
重啟防火牆
firewall-cmd --reload #重啟firewall
systemctl stop firewalld.service #停止firewall
systemctl disable firewalld.service #禁止firewall開機啟動- 1
- 2
- 3
CentOS 7 以下版本 iptables 命令
如要開放80,22,8080 埠,輸入以下命令即可
/sbin/iptables -I INPUT -p tcp --dport 80 -j ACCEPT
/sbin/iptables -I INPUT -p tcp --dport 22 -j ACCEPT
/sbin/iptables -I INPUT -p tcp --dport 8080 -j ACCEPT- 1
- 2
- 3
然後儲存:
/etc/rc.d/init.d/iptables save- 1
檢視開啟的埠:
/etc/init.d/iptables status- 1
關閉防火牆
1) 永久性生效,重啟後不會復原
開啟: chkconfig iptables on
關閉: chkconfig iptables off
2) 即時生效,重啟後復原
開啟: service iptables start
關閉: service iptables stop
六:啟動svn伺服器
在跟目錄下,執行如下命令:
>svnserve -d -r /var/svn/svnrepos
啟動成功後,可用ps -aux檢視服務啟動是否成功
七:客戶端訪問svn伺服器
在windows客戶端,輸入地址:svn://ip地址:3690/xxxx (iP地址為你linux的ip,xxxx為前文建立的版本庫名稱,3690為svn預設埠)
彈出輸入使用者名稱和密碼,輸入即可訪問
二 建立分支
1,建立分支
svn copy http://example.com/repos/project/trunk http://example.com/repos/project/branches/beta
2,合併分支到主幹
在分支上,獲取剛開始的版本號
svn log --stop-on-copy http://example.com/repos/project/branches/search_collect_1108
如得到版本號為:12461
在分支上,獲取最新的版本號
svn up
如得到版本號為:12767
切換到主幹,然後執行下面命令(後面的路徑為,分支的路徑。)
svn merge -r 12461:12767 http://example.com/repos/project/branches/search_collect_1108
一、建立分支
1,建立一個分支
svn copy svn://xx.com/repo/trunk svn://xx.com/repo/branches/TRY-something -m 'make branches TRY-something'
2,把工作目錄轉到分支
svn switch svn://xx.com/repo/branches/TRY-something
當然,也可以再轉到主幹svn switch svn://xx.com/repo/trunk
二、合併一個分支到主幹
1, 查詢到分支版本
方法一:cd branch
svn log --stop-on-copy
最後一個r11340就是建立分支時的reversion
方法二:cd trunk
命令:svn -q --stop-on-copy 分支URL,這條命令會查詢出自建立分支以後分支上的所有修改,最下面的那個版本號就是我們要找的版本號.
示例:svn log -q --stop-on-copy svn://192.168.1.177/tags/beta_2009_12_24
2, 合併到主幹
命令:svn -r 分支版本號:HEAD 分支的URL
解釋:HEAD為當前主幹上的最新版本
示例:
cd trunk
svn merge -r 12:HEAD svn://192.168.1.177/tags/beta_2009_12_24
解決衝突:
使用svn st | grep ^C 查詢合併時的衝突檔案,手工解決衝突
使用svn resolved filename 告知svn衝突已解決
使用svn commit -m "" 提示合併後的版本
svn: Aborting commit: '/path/resources/noc' remains in conflict
$ svn revert resources/noc
Reverted 'resources/noc'
以下是我的authz,passwd,svnserve.conf檔案部分內容
authz:
### This file is an example authorization file for svnserve.
### Its format is identical to that of mod_authz_svn authorization
### files.
### As shown below each section defines authorizations for the path and
### (optional) repository specified by the section name.
### The authorizations follow. An authorization line can refer to:
### - a single user,
### - a group of users defined in a special [groups] section,
### - an alias defined in a special [aliases] section,
### - all authenticated users, using the '$authenticated' token,
### - only anonymous users, using the '$anonymous' token,
### - anyone, using the '*' wildcard.
###
### A match can be inverted by prefixing the rule with '~'. Rules can
### grant read ('r') access, read-write ('rw') access, or no access
### ('').
[aliases]
# joe = /C=XZ/ST=Dessert/L=Snake City/O=Snake Oil, Ltd./OU=Research Institute/CN=Joe Average
[groups]
# harry_and_sally = harry,sally
# harry_sally_and_joe = harry,sally,&joe
admin=root
# [/foo/bar]
# harry = rw
# &joe = r
# * =
# [repository:/baz/fuz]
# @harry_and_sally = rw
# * = r
[/]
@admin=rw
*=
passwd:
### This file is an example password file for svnserve.
### Its format is similar to that of svnserve.conf. As shown in the
### example below it contains one section labelled [users].
### The name and password for each user follow, one account per line.
[users]
# harry = harryssecret
# sally = sallyssecret
root=root
svnserve.conf:
### This file controls the configuration of the svnserve daemon, if you
### use it to allow access to this repository. (If you only allow
### access through http: and/or file: URLs, then this file is
### irrelevant.)
### Visit http://subversion.apache.org/ for more information.
[general]
### The anon-access and auth-access options control access to the
### repository for unauthenticated (a.k.a. anonymous) users and
### authenticated users, respectively.
### Valid values are "write", "read", and "none".
### Setting the value to "none" prohibits both reading and writing;
### "read" allows read-only access, and "write" allows complete
### read/write access to the repository.
### The sample settings below are the defaults and specify that anonymous
### users have read-only access to the repository, while authenticated
### users have read and write access to the repository.
anon-access = none
auth-access = write
### The password-db option controls the location of the password
### database file. Unless you specify a path starting with a /,
### the file's location is relative to the directory containing
### this configuration file.
### If SASL is enabled (see below), this file will NOT be used.
### Uncomment the line below to use the default password file.
password-db = passwd
### The authz-db option controls the location of the authorization
### rules for path-based access control. Unless you specify a path
### starting with a /, the file's location is relative to the the
### directory containing this file. If you don't specify an
### authz-db, no path-based access control is done.
### Uncomment the line below to use the default authorization file.
authz-db = authz
### This option specifies the authentication realm of the repository.
### If two repositories have the same authentication realm, they should
### have the same password database, and vice versa. The default realm
### is repository's uuid.
# realm = My First Repository
### The force-username-case option causes svnserve to case-normalize
### usernames before comparing them against the authorization rules in the
### authz-db file configured above. Valid values are "upper" (to upper-
### case the usernames), "lower" (to lowercase the usernames), and
### "none" (to compare usernames as-is without case conversion, which
### is the default behavior).
# force-username-case = none
[sasl]
### This option specifies whether you want to use the Cyrus SASL
### library for authentication. Default is false.
### This section will be ignored if svnserve is not built with Cyrus
### SASL support; to check, run 'svnserve --version' and look for a line
### reading 'Cyrus SASL authentication is available.'
# use-sasl = true
### These options specify the desired strength of the security layer
### that you want SASL to provide. 0 means no encryption, 1 means
### integrity-checking only, values larger than 1 are correlated
### to the effective key length for encryption (e.g. 128 means 128-bit
### encryption). The values below are the defaults.
# min-encryption = 0
# max-encryption = 256
