SSL/TLS深度解析--OpenSSL的基本使用
阿新 • • 發佈:2018-10-30
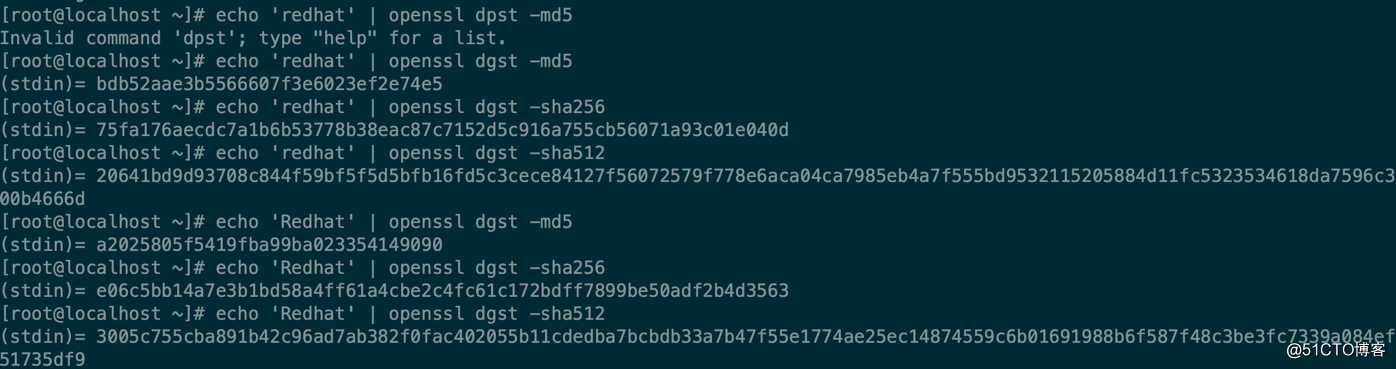
with xiv ppc mes fall ble 默認 bcg otl 摘要算法
[root@localhost ~]# openssl dgst -help #默認sha256 Usage: dgst [options] [file...] file... files to digest (default is stdin) -help Display this summary -c Print the digest with separating colons -r Print the digest in coreutils format -out outfile Output to filename rather than stdout -passin val Input file pass phrase source -sign val Sign digest using private key #簽名,使用RSA DSA ECDSA私鑰簽名 -verify val Verify a signature using public key #使用公鑰驗證簽名 -prverify val Verify a signature using private key -signature infile File with signature to verify #簽名文件(與verify合用) -keyform format Key file format (PEM or ENGINE) -hex Print as hex dump #十六進制輸出,默認就是-hex -binary Print in binary form -d Print debug info -debug Print debug info -fips-fingerprint Compute HMAC with the key used in OpenSSL-FIPS fingerprint -hmac val Create hashed MAC with key -mac val Create MAC (not necessarily HMAC) -sigopt val Signature parameter in n:v form -macopt val MAC algorithm parameters in n:v form or key -* Any supported digest -rand val Load the file(s) into the random number generator -writerand outfile Write random data to the specified file -engine val Use engine e, possibly a hardware device [root@localhost ~]# echo ‘redhat‘ | openssl dgst -md5 (stdin)= bdb52aae3b5566607f3e6023ef2e74e5 [root@localhost ~]# echo ‘redhat‘ | openssl dgst -sha256 (stdin)= 75fa176aecdc7a1b6b53778b38eac87c7152d5c916a755cb56071a93c01e040d [root@localhost ~]# echo ‘redhat‘ | openssl dgst -sha512 (stdin)= 20641bd9d93708c844f59bf5f5d5bfb16fd5c3cece84127f56072579f778e6aca04ca7985eb4a7f555bd9532115205884d11fc5323534618da7596c300b4666d [root@localhost ~]# echo ‘Redhat‘ | openssl dgst -md5 (stdin)= a2025805f5419fba99ba023354149090 [root@localhost ~]# echo ‘Redhat‘ | openssl dgst -sha256 (stdin)= e06c5bb14a7e3b1bd58a4ff61a4cbe2c4fc61c172bdff7899be50adf2b4d3563 [root@localhost ~]# echo ‘Redhat‘ | openssl dgst -sha512 (stdin)= 3005c755cba891b42c96ad7ab382f0fac402055b11cdedba7bcbdb33a7b47f55e1774ae25ec14874559c6b01691988b6f587f48c3be3fc7339a084ef51735df9
對稱加密
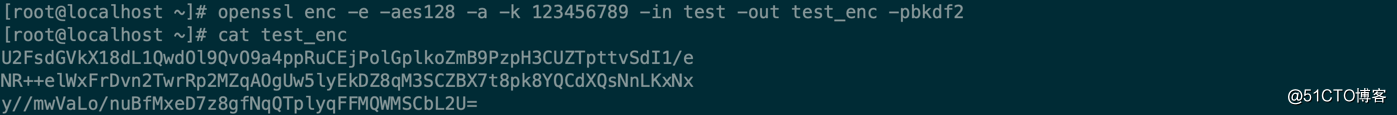
[root@localhost ~]# openssl enc -help Usage: enc [options] Valid options are: -help Display this summary -ciphers List ciphers -in infile Input file -out outfile Output file -pass val Passphrase source -e Encrypt -d Decrypt -p Print the iv/key -P Print the iv/key and exit -v Verbose output -nopad Disable standard block padding -salt Use salt in the KDF (default) -nosalt Do not use salt in the KDF -debug Print debug info -a Base64 encode/decode, depending on encryption flag -base64 Same as option -a -A Used with -[base64|a] to specify base64 buffer as a single line -bufsize val Buffer size -k val Passphrase -kfile infile Read passphrase from file -K val Raw key, in hex -S val Salt, in hex -iv val IV in hex -md val Use specified digest to create a key from the passphrase -iter +int Specify the iteration count and force use of PBKDF2 -pbkdf2 Use password-based key derivation function 2 -none Don‘t encrypt -* Any supported cipher -rand val Load the file(s) into the random number generator -writerand outfile Write random data to the specified file -z Use zlib as the ‘encryption‘ -engine val Use engine, possibly a hardware device [root@localhost ~]# openssl enc -ciphers Supported ciphers: -aes-128-cbc -aes-128-cfb -aes-128-cfb1 -aes-128-cfb8 -aes-128-ctr -aes-128-ecb -aes-128-ofb -aes-192-cbc -aes-192-cfb -aes-192-cfb1 -aes-192-cfb8 -aes-192-ctr -aes-192-ecb -aes-192-ofb -aes-256-cbc -aes-256-cfb -aes-256-cfb1 -aes-256-cfb8 -aes-256-ctr -aes-256-ecb -aes-256-ofb -aes128 -aes128-wrap -aes192 -aes192-wrap -aes256 -aes256-wrap -aria-128-cbc -aria-128-cfb -aria-128-cfb1 -aria-128-cfb8 -aria-128-ctr -aria-128-ecb -aria-128-ofb -aria-192-cbc -aria-192-cfb -aria-192-cfb1 -aria-192-cfb8 -aria-192-ctr -aria-192-ecb -aria-192-ofb -aria-256-cbc -aria-256-cfb -aria-256-cfb1 -aria-256-cfb8 -aria-256-ctr -aria-256-ecb -aria-256-ofb -aria128 -aria192 -aria256 -bf -bf-cbc -bf-cfb -bf-ecb -bf-ofb -blowfish -camellia-128-cbc -camellia-128-cfb -camellia-128-cfb1 -camellia-128-cfb8 -camellia-128-ctr -camellia-128-ecb -camellia-128-ofb -camellia-192-cbc -camellia-192-cfb -camellia-192-cfb1 -camellia-192-cfb8 -camellia-192-ctr -camellia-192-ecb -camellia-192-ofb -camellia-256-cbc -camellia-256-cfb -camellia-256-cfb1 -camellia-256-cfb8 -camellia-256-ctr -camellia-256-ecb -camellia-256-ofb -camellia128 -camellia192 -camellia256 -cast -cast-cbc -cast5-cbc -cast5-cfb -cast5-ecb -cast5-ofb -chacha20 -des -des-cbc -des-cfb -des-cfb1 -des-cfb8 -des-ecb -des-ede -des-ede-cbc -des-ede-cfb -des-ede-ecb -des-ede-ofb -des-ede3 -des-ede3-cbc -des-ede3-cfb -des-ede3-cfb1 -des-ede3-cfb8 -des-ede3-ecb -des-ede3-ofb -des-ofb -des3 -des3-wrap -desx -desx-cbc -id-aes128-wrap -id-aes128-wrap-pad -id-aes192-wrap -id-aes192-wrap-pad -id-aes256-wrap -id-aes256-wrap-pad -id-smime-alg-CMS3DESwrap -idea -idea-cbc -idea-cfb -idea-ecb -idea-ofb -rc2 -rc2-128 -rc2-40 -rc2-40-cbc -rc2-64 -rc2-64-cbc -rc2-cbc -rc2-cfb -rc2-ecb -rc2-ofb -rc4 -rc4-40 -seed -seed-cbc -seed-cfb -seed-ecb -seed-ofb -sm4 -sm4-cbc -sm4-cfb -sm4-ctr -sm4-ecb -sm4-ofb
[root@localhost ~]# cat test 0123456789 alnkldljkdldjslflslsls ldljfdsnjldsjlffsdlfj fldfjdsfflsdfjsdljflsdfjl jlfjldsfjjodsfjwej2o99ojkl [root@localhost ~]# openssl enc -e -aes128 -a -k 123456789 -in test -out test_enc -pbkdf2 [root@localhost ~]# cat test_enc U2FsdGVkX1/Y3xaAkBV42ZQXSrMuasKjq9jYRonHmE3YXv5qcv7rzxOpNxX09DrR JmBbjzGF6dMmLBfaPIfm6x0ajzHzBojlfRM4Ulq+KUximcCe8X7+sm00ldtvVe21 KnTP85W/vFtmIR0cgARVhrWf94sboXm+ubIV+Qo1jK0= [root@localhost ~]# openssl enc -d -aes128 -a -k 123456789 -in test_enc -out test_des #解密 [root@localhost ~]# openssl enc -e -aes128 -a -pass pass:123456789 -in test -out test_enc1 -pbkdf2 [root@localhost ~]# openssl enc -d -aes128 -a -pass pass:123456789 -in test_enc1 -out test_des1 [root@localhost ~]# openssl enc -e -aes128 -a -pass pass:123456789 -in test -out test_enc1 -p salt=3834AB80CB0D45C9 key=25E62D924ACE8BD4F8CC4429CCD54875 iv =072829CEACAD01641D63EAEF58723C01 # -pass pass:123456 對應-k # -pass file:passwd.txt 對應-kfile # -pass env:passwd:使用環境變量;env表示環境變量 # -pass stdin 使用標準輸入,默認是使用標準輸入 # -pass fd:1 使用文件描述符,fd表示文件描述符
RSA非對稱加密
- 生成私鑰
使用 genrsa 來生成私鑰
-aes256 是使用aes256加密這個私鑰
-passout 是加密的密鑰
-out 指明輸出文件
2048是私鑰的長度,這個2048 是放在最後的。老版本默認是1024位
還有DER格式,生成的私鑰是Base64編碼的,perm格式使用的是base64編碼。
[root@localhost ~]# mkdir rsa
[root@localhost ~]# cd rsa
[root@localhost rsa]# openssl genrsa -aes256 -passout pass:test123 -out test_rsa_aes_prikey 2048
Generating RSA private key, 2048 bit long modulus (2 primes)
................................................+++++
......................+++++
e is 65537 (0x010001) #公鑰指數, e值表示公用指數,默認情況下會被設置為65537。這是所謂的短公用指數(short public exponent),它可以顯著提高RSA的驗證性能。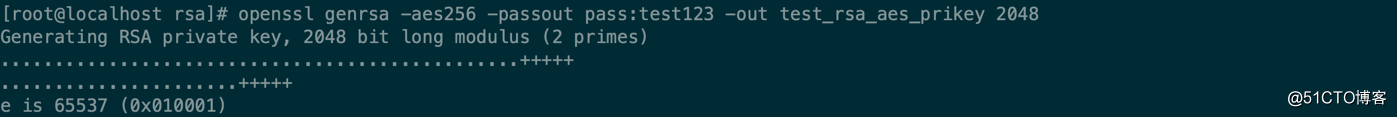
[root@localhost rsa]# cat test_rsa_aes_prikey
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-256-CBC,EE88B4C778CCBFE0ADCA542815FAD479
lWXpOQOSHHmjHi7bRJTfuocwVw3r485E+zqnxOoMe3b5UW07L/3He5MKn6LwS7qc
jiHqoDKwXp00E5vOvegnR6LPK/pO3GPB5P+B0FiAn/wWv2pZ+OvIiq7xF3IQ+l5u
qazf2qLnR4nPlVn9slLNFNhun6gDDWLMkW+4GoD5CelAGlqEVX3XmhAfHv5SnCqV
tL3cT2lH8Y39jztgak7BEmDrLMBlGV0kK537otQW+8LgAtGqQbnmG6HXe15zm64o
WmF0abQ2iopOjGIoq0G+LpdezHiCvo/HWA6Rrle/Le0wN7ri7btOR5MBr8dT94rd
q+OiHixti124+GIJoPPCDCuCjJhNObXMYPRnRHZxP29eM4RKaRzy9bJ53ygnf37P
ozOK+qoIl0qWALuqPOq5DG+8MzMyUO6mOaWtyxWnQkYwz9SrqGVsdFZnMJtW1Ys/
/LAxiZ61M/U5Bf4YhPriz0U3eltZt0m/CGGXy61bEXS+ezZ/bQckbXgsKsk7LhiI
v0Qhufhw5lCzGpYu+RAmMq/+DeGqYtmf3G4tC3xo6k+iqZ52pX2OUPzYgsaQl1k0
YUMWn3NrWfWYwdI6xcZ/UXESbcVfaMQgu5NFxaXOqmO0Fw7qkMVR18GtbIjpkST4
GG+N2x+jxziPau6/3aFX7jgLl/ctyLr5xIzX7B5QEVLQkiwzunInqZpStYQj2h1H
Tc+vS/51QBFL6pTv2QbTfROJG471183sqt77wq+EPKyuAUSMo/6FmUOS5tdhShmT
+ucH7uqDKLPM5etXsA/1uUFQJALJtuy1AIDljyuXOswtjU7bCmrfEDjVIzOpgpQ+
CTPsWT42Cp1ylH7vPFqIdvSTM887XDDbX/c5UEeejlreTBF9J5pZJ+v9WQ4risqp
3rhhvtm3o4ud7DOXVFeDNURJ+QFjxb+Bw2mf0WDldP/c6EBDotqxL0Uo5q4FiUvF
jIh3AU7uVkiOPS/33jwUXOaobmEcS5ibj74ubrE8Ka5cVoQCleaMWnxYZV+O3Ovy
YFBaDV8o6luiMpCYy4Ba+veHLT6Neye0D1NlHdC/NcAr1frWLFpgyro+rJ7gEFII
1CtR3Nvw/PPK9Jd6pXCIY6d4MMZDrYIafhDGRnASW4e2rv5N20mHjg8qu7laLNl/
UlbuLfBWZUpX5KaBLPFMm7POnktZHaKiDpNUHvfS84ZnF22HAdhz3Bbru1CrKhyI
U4APHrLR+dKuHP+xg4fSPvcgy61ouhnP0X7Q2ibPP2my1M2rPjGxY74bQlwf5HnA
luWzGd5MvYn71/ovMZqi6XY7c2VjEBPYH4dss6EmEiAHXRRYpkSBXq7R2xNRtjHx
AQYg97KxqJzJqk2iKERktZSVkOppMl9aQfezZvIK5toYB1a6gKkqjyOD8TbMWfp/
uPJnJE6JtcOh1ba++nFlUvUKZ6MdskdDahOdl3rixuxUBx/Q8RRF7VMLIk1dXb8k
l3fS1sqzfwEMJjLay2eU1BPCkvkxKGBtwZlo0LByjzKZseyH13G222XUOJv4p+uk
tgXPdC74B3DBkRR/X7JfIfa/yrg6FJvIXzasH3QHlz9ECoxe90xDFMOt+0wD9a4X
-----END RSA PRIVATE KEY-----
[root@localhost rsa]# openssl rsa -in test_rsa_aes_prikey
Enter pass phrase for test_rsa_aes_prikey:
writing RSA key
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAm4J/cx6HD/AUTkRum6fOwsyuP6GO8iIhFemCZVXIPAMLq+I6
RJI1rre4DQUe8JN0/WeLE/8V3v7SLSqY/hKpheR62CnUn5VQuxk56sCPgBV0HfBg
NnUjP30G57N5OREpRUvgkg13YXCFGxm+gBoIfpcKgFsTvcx18GvXmorpwZjmjuf+
dSftwYeyJ2Ylk8uAWvJFQziN6WBjhiPnIHauUxAvSKPWvvZYocxKh2FALLKoop2+
G7NWP4NuvQw+bo1vgJwxWJUgUx3v2amvMNs1iOqYU496RFLHygCjUQ+zEblCbrwo
d4RNUNpA4ApTXyVd/o11x2tf6b4DferPAM6dNwIDAQABAoIBAGvQvQYWSzOskpd0
8G6wmDQMbl6lZxLOwLuNap9RKwMYZXYk4Zr694cLzuoP+9R1l2285PrXJtW1PAie
ePXmAGxY7SaDUevWPOOK6NGt8Y+u0BOVvU7kRazVxPzNPKVpFYD6y1bXSUZgGZih
b6cm5W7GzzwQaQ50++vVCOUXnFtgzwI99dSviilsomxsekdgVTdaU5VOErcUg/kc
6+QUUBJRJKnp0O+3gGDiY1QcyeTDIZ7CjaHjow1q+s5bxRRo9n4tHUWoaf3izvDm
5SWYwCkuFWb8Pc7o0X2c2wC2zWq4JaraswXsXfQ8Y3m9zFafeyyKHJNJnBt4vnGc
dg9OmZkCgYEAyXzuUrJKMYINpgzGG+jnKOuYT1Ieogin9q4iBgIfzaqM581j8LOD
TK3EeGI6v0iTavI49bG6udu0+15Wi1a/aiIZFNqZGzEnc4NxVw+hyZT+cUczFHC0
Rd+WzO4VkALhshG8SiWknVO3hFQptOb7g5VEo1Epm/TY3jFaLFrPub0CgYEAxZUc
Yfd+Ljuvo/HXBIkfdpaNCl4lon3oLh1upxkH5CdNlez9V8uzrnDP2vzqhaM6O24r
KmPHFMlHGvIAMTIx68t9llf9RdbnzdNT7z3ALmZcyaUBBhzH8dBHuYUAwxI8fJk8
7qwdOX+sBTtuXmgM/v5s0uegcJ2OEevQwn58MAMCgYB/mb7UYFTcRaCfKDfONREv
uQQcN8VumEzGzEB/zZiWhwv1QP2p0gW06dci5hKOUUgK0pt//a5jReC30Ga+l5Fh
hXac3lNYBSkW3odIu32aS+FXm9+dckK4fYDjB2Rgb3K/crvruSsm932hMCu5hQ6D
pmRxiVTwj39IN7kDnf8vgQKBgCWcI6H2VXuBewaPE2nWnDmboM9XanyK0PZuPdDq
79ibLqaaTQM4UESlTruVpyK3Fm+XofnYsl2fjrxvUmAK+Pu0aXyD1T9FECzazEBf
FcT/USxFD3PVaK38Apsq2SFIyGDDXpjkBFAcoGcCkBjCX67uSVLAKoclRpTcuYk8
QHF3AoGBAIla5lKv5mpAx8WZBJGnifEwXDiizzbrFiCyzgUTL3zn1Idr+V8OAfGZ
aYBa89DO4bP176L3ptKt/PK09o/2NTQSuYGCMeBQuC9SRdvviMyPyrGdPVuCFTU7
Y5zWioAOGECglWjwvQyw07+Tg27vyt+hLemXCArwosBElqqFYBv9
-----END RSA PRIVATE KEY-----
[root@localhost rsa]# openssl rsa -pubout -in test_rsa_aes_prikey
Enter pass phrase for test_rsa_aes_prikey:
writing RSA key
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAm4J/cx6HD/AUTkRum6fO
wsyuP6GO8iIhFemCZVXIPAMLq+I6RJI1rre4DQUe8JN0/WeLE/8V3v7SLSqY/hKp
heR62CnUn5VQuxk56sCPgBV0HfBgNnUjP30G57N5OREpRUvgkg13YXCFGxm+gBoI
fpcKgFsTvcx18GvXmorpwZjmjuf+dSftwYeyJ2Ylk8uAWvJFQziN6WBjhiPnIHau
UxAvSKPWvvZYocxKh2FALLKoop2+G7NWP4NuvQw+bo1vgJwxWJUgUx3v2amvMNs1
iOqYU496RFLHygCjUQ+zEblCbrwod4RNUNpA4ApTXyVd/o11x2tf6b4DferPAM6d
NwIDAQAB
-----END PUBLIC KEY-----[root@localhost rsa]# openssl rsa --help
Usage: rsa [options]
Valid options are:
-help Display this summary
-inform format Input format, one of DER NET PEM
-outform format Output format, one of DER NET PEM PVK
-in val Input file #指定輸入文件;默認in後面指定的是一個私鑰信息
-out outfile Output file #指定輸出的文件
-pubin Expect a public key in input file #讀取公鑰信息 ;如果-in指定的是一個公鑰;默認in指定的是一個私鑰信息
-pubout Output a public key #輸出公鑰信息;根據私鑰的信息得出公鑰
-passout val Output file pass phrase source #私鑰密碼;用於將非加密的私鑰轉換成加密的私鑰
-passin val Input file pass phrase source #私鑰生成時的私鑰密碼 ; 用於將加密的私鑰解密
-RSAPublicKey_in Input is an RSAPublicKey
-RSAPublicKey_out Output is an RSAPublicKey
-noout Don‘t print key out #不輸出私鑰(或公鑰)本身
-text Print the key in text #以文本形式顯示
-modulus Print the RSA key modulus
-check Verify key consistency
-* Any supported cipher
-pvk-strong Enable ‘Strong‘ PVK encoding level (default)
-pvk-weak Enable ‘Weak‘ PVK encoding level
-pvk-none Don‘t enforce PVK encoding
-engine val Use engine, possibly a hardware device
[root@localhost rsa]# openssl rsa -in test_rsa_aes_prikey -passout pass:test123 -out enc_rsa_2048_prikey
Enter pass phrase for test_rsa_aes_prikey:
writing RSA key
[root@localhost rsa]# openssl rsa -pubout -in enc_rsa_2048_prikey
writing RSA key
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAm4J/cx6HD/AUTkRum6fO
wsyuP6GO8iIhFemCZVXIPAMLq+I6RJI1rre4DQUe8JN0/WeLE/8V3v7SLSqY/hKp
heR62CnUn5VQuxk56sCPgBV0HfBgNnUjP30G57N5OREpRUvgkg13YXCFGxm+gBoI
fpcKgFsTvcx18GvXmorpwZjmjuf+dSftwYeyJ2Ylk8uAWvJFQziN6WBjhiPnIHau
UxAvSKPWvvZYocxKh2FALLKoop2+G7NWP4NuvQw+bo1vgJwxWJUgUx3v2amvMNs1
iOqYU496RFLHygCjUQ+zEblCbrwod4RNUNpA4ApTXyVd/o11x2tf6b4DferPAM6d
NwIDAQAB
-----END PUBLIC KEY-----
[root@localhost rsa]# openssl rsa -in test_rsa_aes_prikey -ase128 -passout pass:test123 -out enc_rsa_2048_prikey
#私鑰是否加密是可以生成之後再改變的- 格式轉換
#默認是pem 格式 轉換成der格式
[root@localhost rsa]# openssl rsa -in test_rsa_aes_prikey -outform der -out 2048prikey.der
Enter pass phrase for test_rsa_aes_prikey:
writing RSA key
#將der格式轉換為pem格式
[root@localhost rsa]# openssl rsa -in 2048prikey.der -inform der -outform pem -out 2048prikey.pem
writing RSA key
#pkcs8 格式轉換 默認 pem 格式
[root@localhost rsa]# openssl pkcs8 -topk8 -inform pem -in test_rsa_aes_prikey -outform pem -nocrypt
Enter pass phrase for test_rsa_aes_prikey:
3.使用公鑰和私鑰進行解密解密
[root@localhost rsa]# openssl rsautl -help
Usage: rsautl [options]
Valid options are:
-help Display this summary
-in infile Input file #輸入文件(待加密或待解密的文件)
-out outfile Output file #輸出文件,加密解密後的文件
-inkey val Input key #密鑰輸入
-keyform PEM|DER|ENGINE Private key format - default PEM #私鑰格式
-pubin Input is an RSA public #表明輸入的是公鑰(默認是私鑰)
-certin Input is a cert carrying an RSA public key #指定證書(從證書讀取公鑰)
-ssl Use SSL v2 padding
-raw Use no padding #無填充,加密的文件要是117或 245字節(正好117或245個字節)
-pkcs Use PKCS#1 v1.5 padding (default)
-oaep Use PKCS#1 OAEP
-sign Sign with private key #表明使用私鑰簽名
-verify Verify with public key #表明使用公鑰驗證簽名
-asn1parse Run output through asn1parse; useful with -verify
-hexdump Hex dump output #以十六進制形式輸出
-x931 Use ANSI X9.31 padding
-rev Reverse the order of the input buffer
-encrypt Encrypt with public key #使用公鑰加密
-decrypt Decrypt with private key #使用私鑰解密
-passin val Input file pass phrase source #輸入文件的自身的密碼
-rand val Load the file(s) into the random number generator
-writerand outfile Write random data to the specified file
-engine val Use engine, possibly a hardware device使用公鑰加密一個文件 能加密的文件的大小和公鑰的大小有關,2048位的公鑰可以加密 (2048) / 8-11 = 245 字節的明文 ,而 1024位的密鑰可以加密 (1024)/ 8 -11 = 117 字節的明文。11 字節是填充信息的元數據。加密後的文件和密鑰的長度一致。如果待加密的文件很小,那麽會使用填充,已達到2048或1024位。
4.ECDSA
生成 ecdsa 私鑰,ecdsa 無法設定密鑰位數,要選擇一個橢圓曲線(-name)
選擇了曲線也就選擇了位數,secp256k1(prime256v1) 就是生成 256位的ECDSA密鑰,openssl有很多條可供選擇的曲線,使用-list_curves選項可以查看所有的橢圓曲線,但是大多數web服務器只支持prime256v1和secp384r1 。256位的密鑰在安全和效率上都很好了,是個平衡的選擇。
- 生成ecdsa私鑰
[root@localhost rsa]# openssl ecparam -genkey -name secp256k1 -out ecprikey.pem
[root@localhost rsa]# ll ecprikey.pem
-rw-------. 1 root root 294 10月 24 10:55 ecprikey.pem
[root@localhost rsa]# openssl ecparam -in ecprikey.pem -text
ASN1 OID: secp256k1
-----BEGIN EC PARAMETERS-----
BgUrgQQACg==
-----END EC PARAMETERS-----
#查看ECDSA私鑰和公鑰
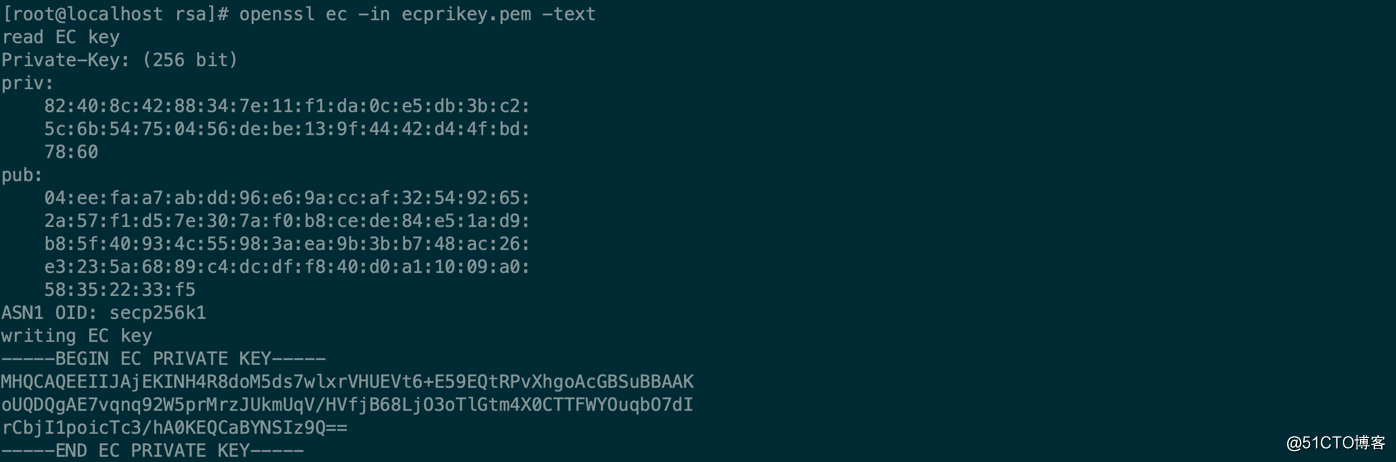
[root@localhost rsa]# openssl ec -in ecprikey.pem -text
read EC key
Private-Key: (256 bit)
priv:
82:40:8c:42:88:34:7e:11:f1:da:0c:e5:db:3b:c2:
5c:6b:54:75:04:56:de:be:13:9f:44:42:d4:4f:bd:
78:60
pub:
04:ee:fa:a7:ab:dd:96:e6:9a:cc:af:32:54:92:65:
2a:57:f1:d5:7e:30:7a:f0:b8:ce:de:84:e5:1a:d9:
b8:5f:40:93:4c:55:98:3a:ea:9b:3b:b7:48:ac:26:
e3:23:5a:68:89:c4:dc:df:f8:40:d0:a1:10:09:a0:
58:35:22:33:f5
ASN1 OID: secp256k1
writing EC key
-----BEGIN EC PRIVATE KEY-----
MHQCAQEEIIJAjEKINH4R8doM5ds7wlxrVHUEVt6+E59EQtRPvXhgoAcGBSuBBAAK
oUQDQgAE7vqnq92W5prMrzJUkmUqV/HVfjB68LjO3oTlGtm4X0CTTFWYOuqbO7dI
rCbjI1poicTc3/hA0KEQCaBYNSIz9Q==
-----END EC PRIVATE KEY-----
#提取公鑰
[root@localhost rsa]# openssl ec -in ecprikey.pem -pubout -out ecpubkey.pem
read EC key
writing EC key
[root@localhost rsa]# cat ecpubkey.pem
-----BEGIN PUBLIC KEY-----
MFYwEAYHKoZIzj0CAQYFK4EEAAoDQgAE7vqnq92W5prMrzJUkmUqV/HVfjB68LjO
3oTlGtm4X0CTTFWYOuqbO7dIrCbjI1poicTc3/hA0KEQCaBYNSIz9Q==
-----END PUBLIC KEY-----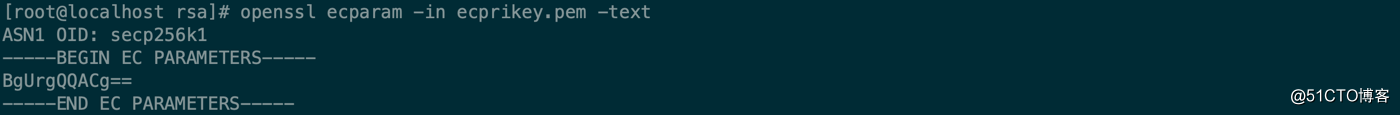
5.數字簽名
[root@localhost rsa]# cat test
dflslsdfjljlasjlsaf
jdsljlsadfljlsdfjljlsdjlsadfl
kldkjfjjflsadjljlsdfjl
12jlk2309933l990kjldsjs
jdljldsljfdljdslfjlsdjlf
lsldjjlsdfjljlsdjdsjkkldjfjkldsjllfdsjlsadjljlkds
[root@localhost rsa]# openssl dgst -sign 2048prikey.pem -sha256 -out sha256_rsa_sign.test test6.其他一些命令
[root@localhost rsa]# openssl speed sha1
Doing sha1 for 3s on 16 size blocks: 18537221 sha1‘s in 2.99s
Doing sha1 for 3s on 64 size blocks: 13406053 sha1‘s in 3.00s
Doing sha1 for 3s on 256 size blocks: 6720935 sha1‘s in 2.99s
Doing sha1 for 3s on 1024 size blocks: 2231335 sha1‘s in 3.00s
Doing sha1 for 3s on 8192 size blocks: 310411 sha1‘s in 2.99s
Doing sha1 for 3s on 16384 size blocks: 159209 sha1‘s in 3.00s
OpenSSL 1.1.1 11 Sep 2018
built on: Sat Oct 20 07:24:19 2018 UTC
options:bn(64,64) rc4(16x,int) des(int) aes(partial) idea(int) blowfish(ptr)
compiler: gcc -fPIC -pthread -m64 -Wa,--noexecstack -Wall -O3 -DOPENSSL_USE_NODELETE -DL_ENDIAN -DOPENSSL_PIC -DOPENSSL_CPUID_OBJ -DOPENSSL_IA32_SSE2 -DOPENSSL_BN_ASM_MONT -DOPENSSL_BN_ASM_MONT5 -DOPENSSL_BN_ASM_GF2m -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DKECCAK1600_ASM -DRC4_ASM -DMD5_ASM -DAES_ASM -DVPAES_ASM -DBSAES_ASM -DGHASH_ASM -DECP_NISTZ256_ASM -DX25519_ASM -DPADLOCK_ASM -DPOLY1305_ASM -DNDEBUG
The ‘numbers‘ are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
sha1 99195.83k 285995.80k 575437.91k 761629.01k 850463.85k 869493.42k
[root@localhost rsa]# openssl speed sha256
Doing sha256 for 3s on 16 size blocks: 13126781 sha256‘s in 2.99s
Doing sha256 for 3s on 64 size blocks: 7492471 sha256‘s in 3.00s
Doing sha256 for 3s on 256 size blocks: 3480299 sha256‘s in 2.99s
Doing sha256 for 3s on 1024 size blocks: 1063047 sha256‘s in 3.00s
Doing sha256 for 3s on 8192 size blocks: 146308 sha256‘s in 2.99s
Doing sha256 for 3s on 16384 size blocks: 73537 sha256‘s in 3.00s
OpenSSL 1.1.1 11 Sep 2018
built on: Sat Oct 20 07:24:19 2018 UTC
options:bn(64,64) rc4(16x,int) des(int) aes(partial) idea(int) blowfish(ptr)
compiler: gcc -fPIC -pthread -m64 -Wa,--noexecstack -Wall -O3 -DOPENSSL_USE_NODELETE -DL_ENDIAN -DOPENSSL_PIC -DOPENSSL_CPUID_OBJ -DOPENSSL_IA32_SSE2 -DOPENSSL_BN_ASM_MONT -DOPENSSL_BN_ASM_MONT5 -DOPENSSL_BN_ASM_GF2m -DSHA1_ASM -DSHA256_ASM -DSHA512_ASM -DKECCAK1600_ASM -DRC4_ASM -DMD5_ASM -DAES_ASM -DVPAES_ASM -DBSAES_ASM -DGHASH_ASM -DECP_NISTZ256_ASM -DX25519_ASM -DPADLOCK_ASM -DPOLY1305_ASM -DNDEBUG
The ‘numbers‘ are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
sha256 70243.64k 159839.38k 297978.78k 362853.38k 400854.56k 401610.07k
[root@localhost rsa]# openssl rand -hex 16
882b85d660d91c5e85cb5b6ea05ca67c
[root@localhost rsa]# openssl rand -base64 16
lGtlf+yGA0EDF85sAl8XEA==
[root@localhost rsa]# openssl rand -hex -out rand.txt 32
[root@localhost rsa]# cat rand.txt
6ae37cf3b7850b9532e153888ab38bd3ca985360ccc4b977d4c07fbeb5d7f49d
SSL/TLS深度解析--OpenSSL的基本使用
