Cisco AP-胖瘦AP的轉換
一、瘦AP到胖AP的轉換:
1、登入到LAP協商的WLC
2、從LAP模式恢復到胖AP,輸入下面命令:config ap tftp tftp_server_ip filename ap_name
注意:需要將映象檔案的字尾修改為.default
3、等待AP重啟並使用CLI或者GUI介面重新配置AP
4、AP自動恢復後,使用者名稱密碼恢復為出廠密碼:cisco;Cisco
5、如下是胖AP的CLI和GUI介面:
Username: cisco
Password:
ap>en
ap>enable
Password:
ap#
ap#
ap#sho ip int br
ap#sho ip int brief
Interface IP-Address OK? Method Status Protocol
BVI1 10.1.1.100 YES TFTP up up
Dot11Radio0 unassigned YES unset administratively down down
Dot11Radio1 unassigned YES unset administratively down down
GigabitEthernet0 unassigned YES TFTP up up
ap#
ap#
ap#
ap#sho ver
ap#sho version
Cisco IOS Software, C1600 Software (AP1G2-K9W7-M), Version 15.3(3)JF1, RELEASE SOFTWARE (fc3)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2017 by Cisco Systems, Inc.
Compiled Fri 20-Oct-17 20:51 by prod_rel_team
ROM: Bootstrap program is C1600 boot loader
BOOTLDR: C1600 Boot Loader (AP1G2-BOOT-M) LoaderVersion 15.2(2)JAX, RELEASE SOFTWARE (fc1)
ap uptime is 1 minute
System returned to ROM by power-on
System image file is "flash:/ap1g2-k9w7-mx.153-3.JF1/ap1g2-k9w7-xx.153-3.JF1"
Last reload reason:
This product contains cryptographic features and is subject to United
States and local country laws governing import, export, transfer and
use. Delivery of Cisco cryptographic products does not imply
third-party authority to import, export, distribute or use encryption.
Importers, exporters, distributors and users are responsible for
compliance with U.S. and local country laws. By using this product you
agree to comply with applicable laws and regulations. If you are unable
to comply with U.S. and local laws, return this product immediately.
A summary of U.S. laws governing Cisco cryptographic products may be found at:
http://www.cisco.com/wwl/export/crypto/tool/stqrg.html
If you require further assistance please contact us by sending email to
[email protected]
使用MODE按鈕和TFTP實現轉換:
注意類似與這種方式,可能會出現AP去尋找的映象檔名和你TFTP server的檔名不一致的情況,一般情況AP尋找的映象就是目前執行的映象,你可以將TFTP server上的檔名從新命名為目前執行的映象名字即可。
1、配置執行TFTP server的PC一個靜態IP,範圍是10.0.0.2-10.0.0.30
2、確保PC的活躍的FTFP server檔案下包含AP的映象檔案
3、在FTFP server資料夾下重新命名AP映象檔案ap3g2-k9w7-tar.default for a 2700 or a 3700 series access point.
4、連線PC和AP使用5類乙太網線
5、斷開AP的電源
6、當你重新給AP上電時按住MODE按鈕
注意:AP上的MODE按鈕必須開啟,參考config ap rst-button {enable | disable} {ap-name}
7、按住MODE按鈕知道狀態燈變紅(大約20-30s),然後釋放MODE按鈕
8、等待AP重啟閃爍綠燈
9、AP重啟後,通過GUI或者CLI介面重新配置
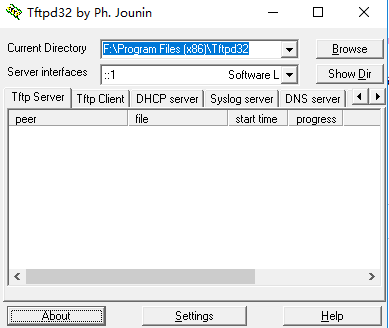
注意:
Ø 最好使用TFTP32工具
Ø 注意筆記本的防火牆
Ø 注意檔名修改為:ap3g2-k9w7-tar.default類似的格式
Ø筆記本的IP地址配置為10.0.0.2-30/24或者10.0.0.2-30/8都可以,不需要配置GW
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
Cisco IOS Software, C1600 Software (AP1G2-K9W7-M), Version 15.3(3)JF1, RELEASE SOFTWARE (fc3)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2017 by Cisco Systems, Inc.
Compiled Fri 20-Oct-17 20:51 by prod_rel_team
Initializing flashfs...
FLASH CHIP: Micron N25Q256
Boot from flash
IOS Bootloader - Starting system.
FLASH CHIP: Micron N25Q256
Xmodem file system is available.
flashfs[0]: 225 files, 8 directories
flashfs[0]: 0 orphaned files, 0 orphaned directories
flashfs[0]: Total bytes: 31936000
flashfs[0]: Bytes used: 12218368
flashfs[0]: Bytes available: 19717632
flashfs[0]: flashfs fsck took 10 seconds.
Reading cookie from SEEPROM
Base Ethernet MAC address: d4:6d:50:af:76:3a
************* loopback_mode = 0
button is pressed, wait for button to be released… //再按著等待15s左右,多等一會兒也沒事
button pressed for 29 seconds
process_config_recovery: set IP address and config to default 10.0.0.1 >>>>IP恢復為10.0.0.1,
process_config_recovery: image recovery
image_recovery: Download default IOS tar image tftp://255.255.255.255/ap1g2-k9w7-tar.default
examining image...
extracting info (282 bytes)
Image info:
Version Suffix: k9w7-.153-3.JF1
Image Name: ap1g2-k9w7-mx.153-3.JF1
Version Directory: ap1g2-k9w7-mx.153-3.JF1
Ios Image Size: 10486272
Total Image Size: 11960832
Image Feature: WIRELESS LAN
Image Family: AP1G2
Wireless Switch Management Version: 8.5.105.0
Extracting files…>>>>>>>>開始提取檔案
ap1g2-k9w7-mx.153-3.JF1/ (directory) 0 (bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/ap1g2-k9w7-mx.153-3.JF1 (123464 bytes)..........................
ap1g2-k9w7-mx.153-3.JF1/html/ (directory) 0 (bytes)
ap1g2-k9w7-mx.153-3.JF1/html/level/ (directory) 0 (bytes)
ap1g2-k9w7-mx.153-3.JF1/html/level/1/ (directory) 0 (bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/appsui.js (563 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/back.shtml (512 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/cookies.js (5032 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/forms.js (20442 bytes)....
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/sitewide.js (17290 bytes)...
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/stylesheet.css (3220 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/config.js (29225 bytes)......
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/popup_capabilitycodes.shtml.gz (1020 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/filter.js.gz (2037 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/filter_vlan.js.gz (1459 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/filter_mac_ether.js.gz (1793 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/security.js.gz (962 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/vlan.js.gz (1196 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/ssid.js.gz (6149 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/network-if.js.gz (2098 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/dot1x.js.gz (988 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/stp.js.gz (957 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/ap_assoc.shtml.gz (5892 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/ap_event-log.shtml.gz (4158 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/ap_home.shtml.gz (7632 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/ap_network-if.shtml.gz (3576 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/ap_network-map.shtml.gz (4124 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/ap_services.shtml.gz (3937 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/ap_system-sw.shtml.gz (3134 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/ap_contextmgr.shtml.gz (4073 bytes)
ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/ (directory) 0 (bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/ap_title_appname.gif (2246 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/1600_title_appname.gif (2826 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/1600_w_title_appname.gif (2351 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/700_w_title_appname.gif (2277 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/700_title_appname.gif (3044 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_button.gif (1211 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_button_1st.gif (1171 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_button_cbottom.gif (318 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_button_current.gif (1206 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_button_endcap.gif (878 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_button_encap_last.gif (333 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_button_last.gif (386 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_button_nth.gif (1177 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_leftnav_dkgreen.gif (869 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_leftnav_green.gif (879 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_leftnav_upright.gif (64 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/apps_leftnav_yellow.gif (881 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/arrowdown_red.gif (108 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/arrowup_green.gif (108 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/corner_ur_7.gif (53 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/dkgreenmask11_up.gif (113 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/dkgreenmask28_upright.gif (110 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/grn_vertlines_bottom.gif (149 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/grn_vertlines_top.gif (141 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/hinav_plus.gif (56 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/left_bkg.gif (146 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/list_data.gif (122 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/logo.gif (29454 bytes)......
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/pixel.gif (49 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/sitewide_downleft.gif (53 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/sitewide_help_off.gif (934 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/sitewide_help_on.gif (934 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/sitewide_print_off.gif (111 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/sitewide_print_on.gif (111 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/spacer.gif (49 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/whitemask11_botleft.gif (62 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/whitemask11_upright.gif (61 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/event_alert.gif (73 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/event_critical.gif (73 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/event_debugging.gif (73 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/event_emergency.gif (73 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/event_error.gif (73 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/event_information.gif (73 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/event_notification.gif (73 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/event_warning.gif (73 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/check_mark.gif (71 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/background_web41.jpg (732 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/cisco-logo-2012.gif (579 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/logout_image.gif (40294 bytes)........
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/itp-logo.png (2822 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/logout_image_itp.gif (48262 bytes)..........
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/cna_icon1.gif (1212 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/cna_icon2.gif (1185 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/cna_icon3.gif (1196 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/cna_icon4.gif (1072 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/1/images/cna_download_splash.gif (44862 bytes).........
ap1g2-k9w7-mx.153-3.JF1/html/level/15/ (directory) 0 (bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_assoc_adv.shtml.gz (4144 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_event-log_config-options.shtml.gz (5730 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_event-log_notif-options.shtml.gz (2693 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_express-setup.shtml.gz (11858 bytes)..
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_express-security.shtml.gz (13550 bytes)...
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/def_broadcast-ssid.shtml.gz (1263 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/def_eap-security.shtml.gz (1791 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/def_no-security.shtml.gz (1582 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/def_wep-security.shtml.gz (1597 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/def_wpa-security.shtml.gz (1854 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_network-if_ipaddress.shtml.gz (6321 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_network-if_802-11.shtml.gz (7132 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_network-if_802-11_b.shtml.gz (6292 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_network-if_802-11_c.shtml.gz (29987 bytes)......
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/dBm_mW_translation_table.shtml.gz (1511 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_network-if_802-11_d.shtml.gz (4070 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_network-if_ethernet.shtml.gz (4377 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_network-if_ethernet_b.shtml.gz (6604 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_network-map_ap-adjacent-list.shtml.gz (3806 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec.shtml.gz (7600 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_ap-client-security.shtml.gz (36305 bytes).......
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_ap-key-security.shtml.gz (12068 bytes)..
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_local-admin-access.shtml.gz (6991 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_network-security_a.shtml.gz (11764 bytes)..
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_network-security_b.shtml.gz (5620 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_lrs.shtml.gz (5087 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_lrs_b.shtml.gz (8525 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_lrs_c.shtml.gz (6205 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_dot1x-security.shtml.gz (6444 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_dot1x-certificates.shtml.gz (11173 bytes)..
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_dot1x-cert_fingerprint.shtml.gz (577 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_ap-client-security-adv_a.shtml.gz (4984 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_ap-client-security-adv_b.shtml.gz (5061 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_ap-client-security-adv_c.shtml.gz (4668 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_ap-client-security-adv_d.shtml.gz (3608 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_band_select.shtml.gz (5720 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_auto-config.shtml.gz (3611 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_ids_mfp.shtml.gz (3922 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_ids_mfp_stats.shtml.gz (3651 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_arp.shtml.gz (3017 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_cdp.shtml.gz (5123 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_console-telnet.shtml.gz (6833 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_dns.shtml.gz (3604 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_filters.shtml.gz (5313 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_filters-ip.shtml.gz (9264 bytes)..
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_filters-mac.shtml.gz (4011 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_filters-ether.shtml.gz (3855 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_hot-standby.shtml.gz (5506 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_http.shtml.gz (6455 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_mobile-ip-b.shtml.gz (6668 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_mobile-ip-c.shtml.gz (4163 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_mobile-ip-d.shtml.gz (5170 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_mobile-ip.shtml.gz (6015 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_qos-traffic.shtml.gz (8139 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_qos.shtml.gz (12217 bytes)..
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_qos_adv.shtml.gz (4443 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_snmp.shtml.gz (8027 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_sntp.shtml.gz (5959 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_vlan.shtml.gz (14651 bytes)...
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_voice-traffic.shtml.gz (6358 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_services_stp.shtml.gz (7128 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_stationview-client_ltest.shtml.gz (5535 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_system-sw_upgrade-b.htm (231 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_system-sw_upgrade-b.shtml.gz (6208 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_system-sw_upgrade.htm (229 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_system-sw_upgrade.shtml.gz (6240 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/banner.html (14136 bytes)...
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/frameAssociation.html (628 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/frameEventlog.html (627 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/frameHome.html (611 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/frameNetWork.html (619 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/frameSecurity.html (637 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/frameServices.html (651 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/frameSoftware.html (650 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/frameWireless.html (626 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/frameset.html (4736 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/navAssociation.html (1269 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/navBar41.css (3605 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/navHome.html (2251 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/navNetwork.html (7057 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/navSecurity.html (2958 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/navServices.html (5018 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/navSoftware.html (1542 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/navWireless.html (1580 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/arrow_down.gif (177 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/arrow_down2.gif (838 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/arrow_right.gif (137 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/arrow_right2.gif (838 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/servicescript41.js.gz (11929 bytes)..
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/sideMenu.js.gz (813 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_easy-setup.shtml.gz (29509 bytes)......
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/navEventLog.html (1283 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/content41.css (10497 bytes)..
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/logout.html (2782 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_guest_list.shtml.gz (2556 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_guest_login.shtml.gz (1523 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_guest_new.shtml.gz (4293 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/frameguest.html (617 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/navguest.html (1605 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_webauth.shtml.gz (4207 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/def_wpa_psk-security.shtml.gz (1859 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/cna_upgrade.htm (5895 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_sec_ap-client-dot11u.shtml.gz (11397 bytes)..
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_system-sw_upgrade_poll.htm (234 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_system-sw_upgrade_poll.shtml (3596 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_system-sw_sysconfig.shtml.gz (7503 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_stationview-client.shtml.gz (5592 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_contextmgr_ap.shtml.gz (4784 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_contextmgr_scm.shtml.gz (5304 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_contextmgr_scm-groups.shtml.gz (7600 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/html/level/15/ap_contextmgr_scm_summary.shtml.gz (5205 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/ap1g2-k9w7-xx.153-3.JF1 (9305273 bytes)...................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................
extracting ap1g2-k9w7-mx.153-3.JF1/8005.img (1174920 bytes)...............................................................................................................................................................................................................................................................
extracting ap1g2-k9w7-mx.153-3.JF1/S2.bin (15184 bytes)...
extracting ap1g2-k9w7-mx.153-3.JF1/S5.bin (128480 bytes)...........................
extracting ap1g2-k9w7-mx.153-3.JF1/K2.bin (8176 bytes).
extracting ap1g2-k9w7-mx.153-3.JF1/K5.bin (98112 bytes).....................
extracting ap1g2-k9w7-mx.153-3.JF1/info (282 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/file_hashes (33037 bytes).......
extracting ap1g2-k9w7-mx.153-3.JF1/final_hash (141 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/final_hash.sig (512 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/img_sign_rel.cert (1375 bytes)
extracting ap1g2-k9w7-mx.153-3.JF1/img_sign_rel_sha2.cert (1371 bytes)
extracting info.ver (282 bytes)
Deleting target version: flash:/ap1g2-k9w7-mx.153-3.JF1...done.
New software image installed in flash:/ap1g2-k9w7-mx.153-3.JF1
Configuring system to use new image...done.
Requested system reload in progress...download took about 453 seconds
Loading "flash:/ap1g2-k9w7-mx.153-3.JF1/ap1g2-k9w7-mx.153-3.JF1"...##############
File "flash:/ap1g2-k9w7-mx.153-3.JF1/ap1g2-k9w7-mx.153-3.JF1" uncompressed and installed, entry point: 0x2004000
executing...
Secondary Bootloader - Starting system.
FLASH CHIP: Micron N25Q256
Xmodem file system is available.
flashfs[0]: 225 files, 8 directories
flashfs[0]: 0 orphaned files, 0 orphaned directories
flashfs[0]: Total bytes: 31936000
flashfs[0]: Bytes used: 12217856
flashfs[0]: Bytes available: 19718144
flashfs[0]: flashfs fsck took 10 seconds.
Reading cookie from SEEPROM
Base Ethernet MAC address: d4:6d:50:af:76:3a
Secondary bootloader Ethernet not enabled, skip ether_init
Boot CMD: 'boot flash:/ap1g2-k9w7-mx.153-3.JF1/ap1g2-k9w7-xx.153-3.JF1;flash:/ap1g2-k9w7-mx.153-3.JF1/ap1g2-k9w7-xx.153-3.JF1'
Loading "flash:/ap1g2-k9w7-mx.153-3.JF1/ap1g2-k9w7-xx.153-3.JF1"...######################################
File "flash:/ap1g2-k9w7-mx.153-3.JF1/ap1g2-k9w7-xx.153-3.JF1" uncompressed and installed, entry point: 0x100000
executing...
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
Cisco IOS Software, C1600 Software (AP1G2-K9W7-M), Version 15.3(3)JF1, RELEASE SOFTWARE (fc3)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2017 by Cisco Systems, Inc.
Compiled Fri 20-Oct-17 20:51 by prod_rel_team
Initializing flashfs...
FLASH CHIP: Micron N25Q256
flashfs[2]: erasing block[0]...
flashfs[2]: erasing block[1]...
flashfs[2]: 225 files, 8 directories
flashfs[2]: 0 orphaned files, 0 orphaned directories
flashfs[2]: Total bytes: 31808000
flashfs[2]: Bytes used: 12217856
flashfs[2]: Bytes available: 19590144
flashfs[2]: flashfs fsck took 13 seconds.
flashfs[2]: Initialization complete.
flashfs[4]: 0 files, 1 directories
flashfs[4]: 0 orphaned files, 0 orphaned directories
flashfs[4]: Total bytes: 11999232
flashfs[4]: Bytes used: 1024
flashfs[4]: Bytes available: 11998208
flashfs[4]: flashfs fsck took 1 seconds.
flashfs[4]: Initialization complete....done Initializing flashfs.
Radio0 present 8764B 8000 0 A8000000 A8010000 0
Rate table has 586 entries (20 legacy/160 11n/406 11ac)
POWER TABLE FILENAME = flash:/ap1g2-k9w7-mx.153-3.JF1/K2.bin
Radio1 present 8764B 8000 0 88000000 88010000 4
POWER TABLE FILENAME = flash:/ap1g2-k9w7-mx.153-3.JF1/K5.bin
This product contains cryptographic features and is subject to United
States and local country laws governing import, export, transfer and
use. Delivery of Cisco cryptographic products does not imply
third-party authority to import, export, distribute or use encryption.
Importers, exporters, distributors and users are responsible for
compliance with U.S. and local country laws. By using this product you
agree to comply with applicable laws and regulations. If you are unable
to comply with U.S. and local laws, return this product immediately.
A summary of U.S. laws governing Cisco cryptographic products may be found at:
http://www.cisco.com/wwl/export/crypto/tool/stqrg.html
If you require further assistance please contact us by sending email to
[email protected]
cisco AIR-SAP1602I-C-K9 (PowerPC) processor (revision B0) with 187386K/74672K bytes of memory.
Processor board ID FGL1849X88Q
PowerPC CPU at 533Mhz, revision number 0x2151
Last reset from power-on
1 Gigabit Ethernet interface
2 802.11 Radios
32K bytes of flash-simulated non-volatile configuration memory.
Base ethernet MAC Address: D4:6D:50:AF:76:3A
Part Number : 73-14671-04
PCB Serial Number : FOC18472W4Q
Top Assembly Part Number : 800-38552-03
Top Assembly Serial Number : FGL1849X88Q
Top Revision Number : A0
Product/Model Number : AIR-CAP1602I-C-K9
Press RETURN to get started!
*Mar 1 00:00:15.555: %SOAP_FIPS-2-SELF_TEST_IOS_SUCCESS: IOS crypto FIPS self test passed (15)
*Mar 1 00:00:22.575: %SOAP_FIPS-2-SELF_TEST_RAD_SUCCESS: RADIO crypto FIPS self test passed on interface Dot11Radio 0 (4)
*Mar 1 00:00:22.719: loading Power Tables from flash:/ap1g2-k9w7-mx.153-3.JF1/K2.bin. Class = E
*Mar 1 00:00:22.719: record size of 3ss: 1168 read_ptr: 2D3D7D6
*Mar 1 00:00:28.995: %SOAP_FIPS-2-SELF_TEST_RAD_SUCCESS: RADIO crypto FIPS self test passed on interface Dot11Radio 1 (4)
*Mar 1 00:00:29.067: loading Power Tables from flash:/ap1g2-k9w7-mx.153-3.JF1/K5.bin. Class = C
*Mar 1 00:00:29.067: record size of 3ss: 1168 read_ptr: 2D3D7D6
*Mar 1 00:00:29.979: SCHED: Ethernet Bridge Process: install watched boolean System Initialized(2D284DC), os:1 ah:0
*Mar 1 00:00:31.763: %LINK-6-UPDOWN: Interface GigabitEthernet0, changed state to up
*Mar 1 00:00:32.771: %LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0, changed state to up
*Mar 1 00:00:33.079: Starting Ethernet promiscuous mode
*Mar 1 00:00:33.111: %DOT11-5-EXPECTED_RADIO_RESET: Restarting Radio interface Dot11Radio0 due to interface reset
*Mar 1 00:00:33.119: %DOT11-5-EXPECTED_RADIO_RESET: Restarting Radio interface Dot11Radio1 due to interface reset
*Mar 1 00:00:33.123: %DOT11-5-EXPECTED_RADIO_RESET: Restarting Radio interface Dot11Radio0 due to interface is getting down
*Mar 1 00:00:33.123: %DOT11-5-EXPECTED_RADIO_RESET: Restarting Radio interface Dot11Radio1 due to interface is getting down
*Mar 1 00:00:33.147: %LINK-5-CHANGED: Interface Dot11Radio0, changed state to administratively down
*Mar 1 00:00:33.147: %LINK-5-CHANGED: Interface Dot11Radio1, changed state to administratively down
*Mar 1 00:00:33.159: %SYS-5-RESTART: System restarted --
Cisco IOS Software, C1600 Software (AP1G2-K9W7-M), Version 15.3(3)JF1, RELEASE SOFTWARE (fc3)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2017 by Cisco Systems, Inc.
Compiled Fri 20-Oct-17 20:51 by prod_rel_team
*Mar 1 00:00:33.159: %SNMP-5-COLDSTART: SNMP agent on host ap is undergoing a cold start
*Mar 1 00:00:33.183: %DOT11-5-EXPECTED_RADIO_RESET: Restarting Radio interface Dot11Radio0 due to interface reset
*Mar 1 00:00:33.183: %DOT11-5-EXPECTED_RADIO_RESET: Restarting Radio interface Dot11Radio1 due to interface reset
*Mar 1 00:00:33.183: SCHED: Ethernet Bridge Process: remove watched boolean System Initialized(2D284DC)
*Mar 1 00:00:33.183: SCHED: Ethernet Bridge Process: install watched queue Soap BVI input queue(59C6B48), os:0 ah:0
*Mar 1 00:00:33.183: No configuration in NVRAM..Auto Install initiated..
*Mar 1 00:00:34.135: %LINEPROTO-5-UPDOWN: Line protocol on Interface BVI1, changed state to up
*Mar 1 00:00:34.143: %LINEPROTO-5-UPDOWN: Line protocol on Interface Dot11Radio0, changed state to down
*Mar 1 00:00:34.147: %LINEPROTO-5-UPDOWN: Line protocol on Interface Dot11Radio1, changed state to down
*Mar 1 00:00:47.827: %CDP_PD-4-POWER_OK: Full power - NEGOTIATED inline power source
ap>
ap>sho ver
Cisco IOS Software, C1600 Software (AP1G2-K9W7-M), Version 15.3(3)JF1, RELEASE SOFTWARE (fc3)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2017 by Cisco Systems, Inc.
Compiled Fri 20-Oct-17 20:51 by prod_rel_team
ROM: Bootstrap program is C1600 boot loader
BOOTLDR: C1600 Boot Loader (AP1G2-BOOT-M) LoaderVersion 15.2(2)JAX, RELEASE SOFTWARE (fc1)
ap uptime is 2 minutes
System returned to ROM by power-on
System image file is "flash:/ap1g2-k9w7-mx.153-3.JF1/ap1g2-k9w7-xx.153-3.JF1"
Last reload reason:
This product contains cryptographic features and is subject to United
States and local country laws governing import, export, transfer and
use. Delivery of Cisco cryptographic products does not imply
third-party authority to import, export, distribute or use encryption.
Importers, exporters, distributors and users are responsible for
compliance with U.S. and local country laws. By using this product you
agree to comply with applicable laws and regulations. If you are unable
to comply with U.S. and local laws, return this product immediately.
A summary of U.S. laws governing Cisco cryptographic products may be found at:
http://www.cisco.com/wwl/export/crypto/tool/stqrg.html
If you require further assistance please contact us by sending email to
[email protected]
cisco AIR-SAP1602I-C-K9 (PowerPC) processor (revision B0) with 187386K/74672K bytes of memory.
Processor board ID FGL1849X88Q
PowerPC CPU at 533Mhz, revision number 0x2151
Last reset from power-on
1 Gigabit Ethernet interface
2 802.11 Radios
32K bytes of flash-simulated non-volatile configuration memory.
Base ethernet MAC Address: D4:6D:50:AF:76:3A
Part Number : 73-14671-04
PCB Serial Number : FOC18472W4Q
Top Assembly Part Number : 800-38552-03
Top Assembly Serial Number : FGL1849X88Q
Top Revision Number : A0
Product/Model Number : AIR-CAP1602I-C-K9
Configuration register is 0xF
