Win7 x64 Vad遍歷模組
阿新 • • 發佈:2018-11-10
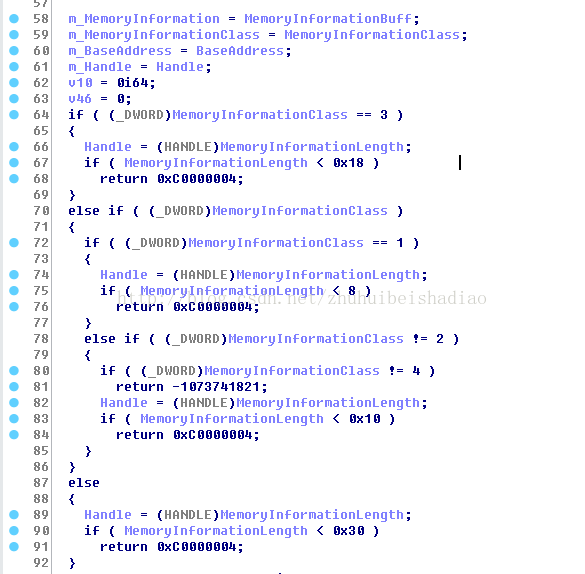
先看下NtQueryVirtualMenmory程式碼
剛開始只是判斷下buff是否符合要求
然後去GS暫存器獲取東西,但發現偏移過去是context,這就無從而知了.
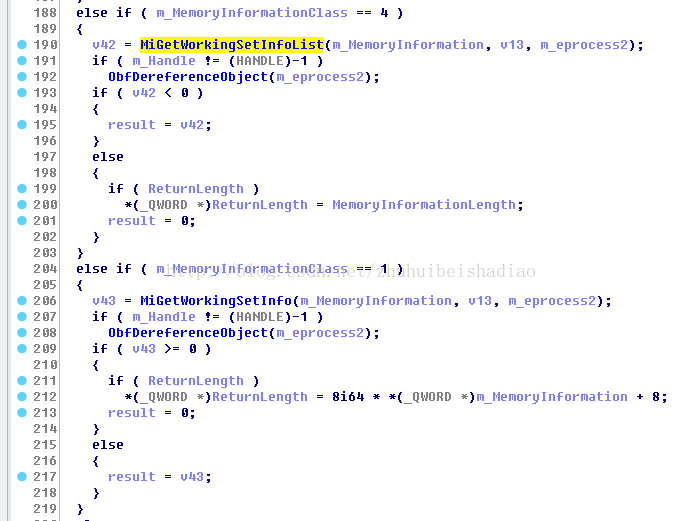
然後去得到EPROCESS 這裡判斷是不是系統程序和buff是否符合要求
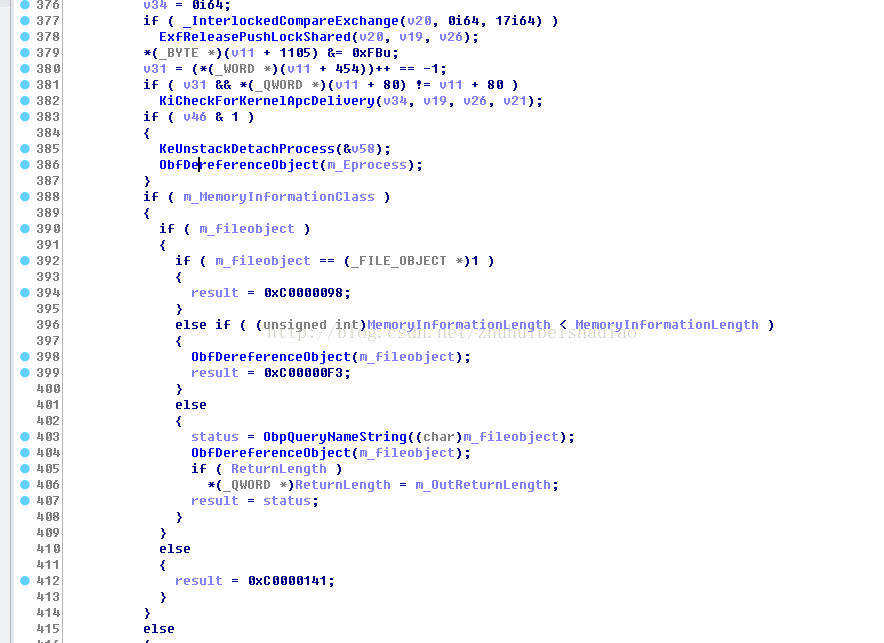
如果是查詢MemoryBasicInformation資訊就填充一些資訊,本篇文章主要是看 MemorySectionName功能(2)
如果是查詢MemoryWorkingSetList和1號功能就呼叫MiGetWorkingSetInfo或者MiGetWorkingSetInfoList
如果都不是1 4 那就是2好功能MemorySectionName
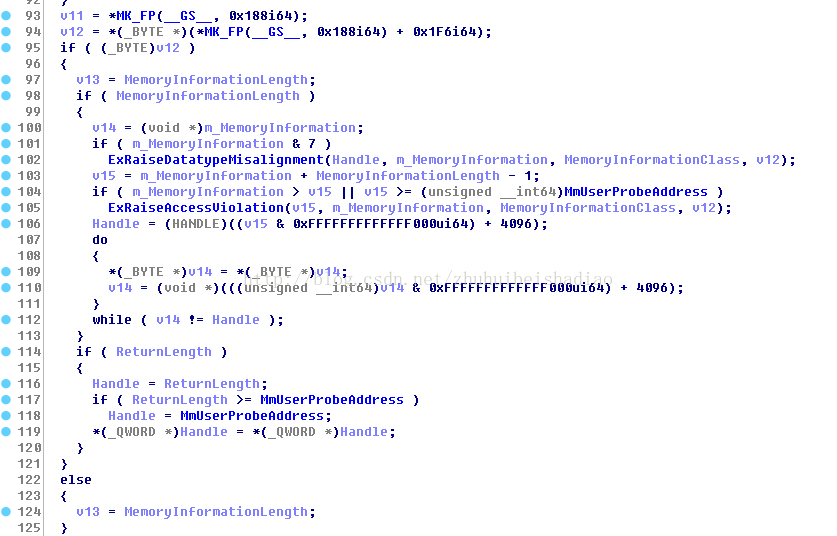
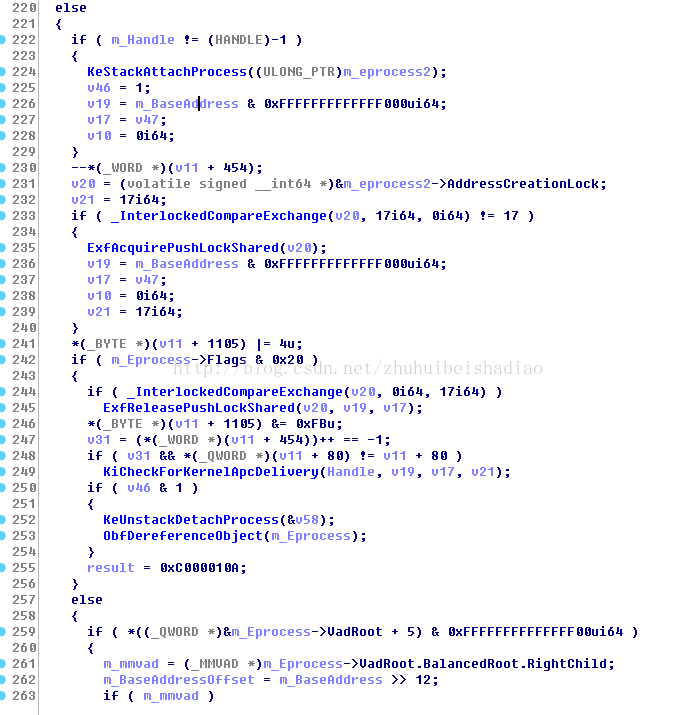
先判斷是不是系統程序 如果不是就KeStackAttachProcess上去
然後獲取鎖鎖住程序
然後判斷如果程序flags是否包含0x20 (VmDeleted ),是就取消附加 解鎖 返回0xC000010A
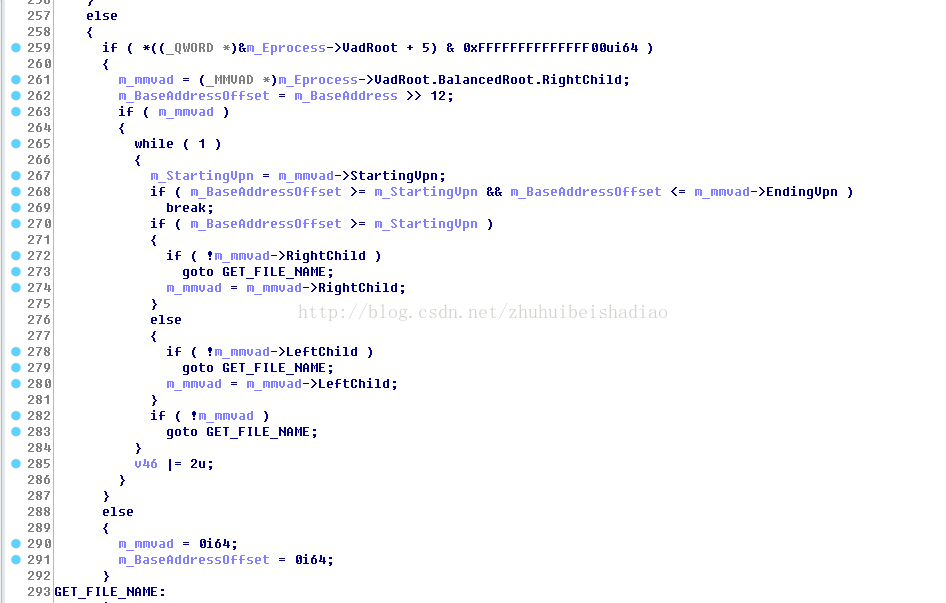
如果程序flags(VmDeleted )是1就去遍歷平衡二叉樹
VadRoot +5 是u成員,不知道是東西,應該跟初始化狀態有關,因為如果是新建立的程序,這個u+5是0,然後過一會就會有值.
期間判斷偏移是否超過正在列舉的模組的大小
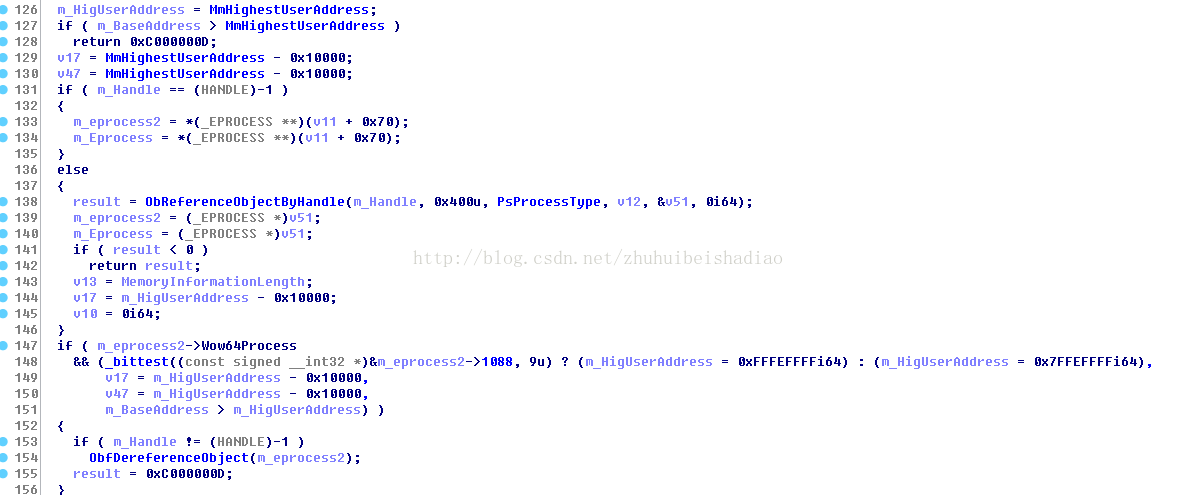
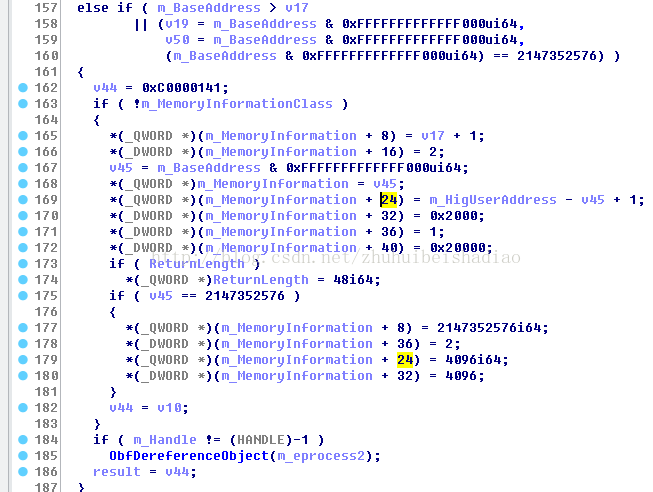
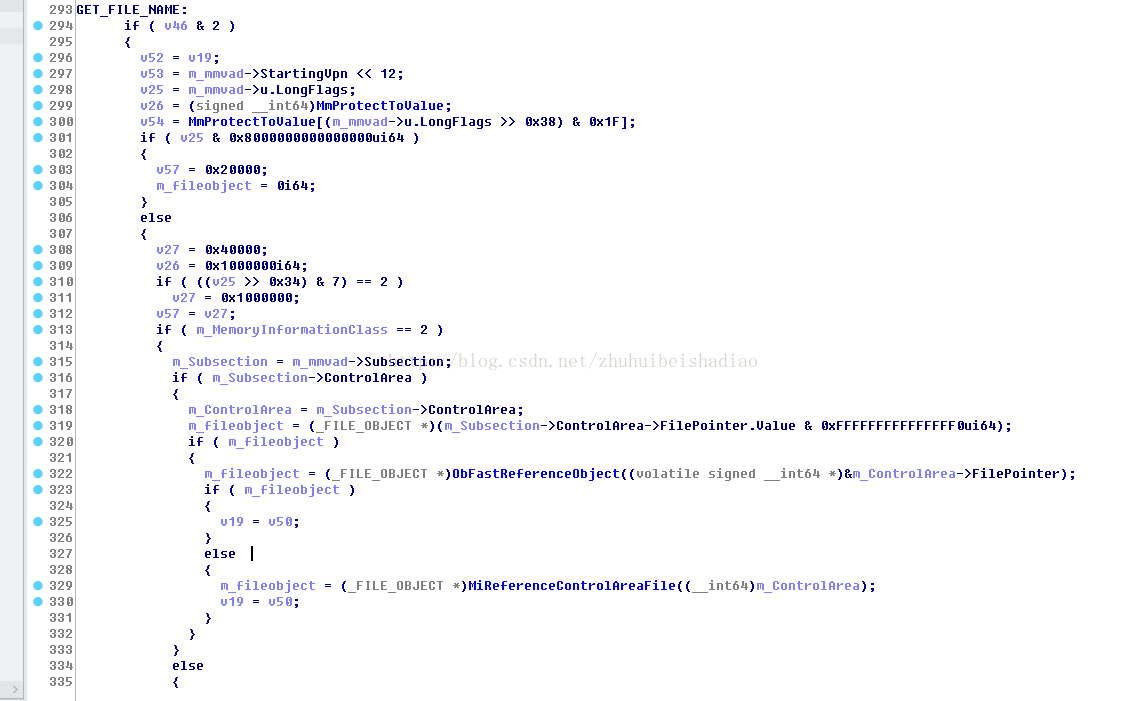
得到節點後就去獲取FILE_OBJECT 上面標籤寫錯了
可以看到是路徑是MMVAD->Subsection->ControlArea->FilePointer.Value 去除後3位
然後呼叫下面2個其中一個函式去鎖住這個物件
如果獲取到FileObject 且不是3號功能
就呼叫ObpQueryNameString查詢檔名
由此 看了之後Windbg看來下
隨便選擇一個程序
1: kd> dt _eprocess 0xfffffa801b104b30 nt!_EPROCESS +0x000 Pcb : _KPROCESS +0x160 ProcessLock : _EX_PUSH_LOCK +0x168 CreateTime : _LARGE_INTEGER 0x01d24a6b`f7e332ad +0x170 ExitTime : _LARGE_INTEGER 0x0 +0x178 RundownProtect : _EX_RUNDOWN_REF +0x180 UniqueProcessId : 0x00000000`00000168 Void +0x188 ActiveProcessLinks : _LIST_ENTRY [ 0xfffffa80`1ab5dcb8 - 0xfffffa80`1b0adcb8 ] +0x198 ProcessQuotaUsage : [2] 0x3858 +0x1a8 ProcessQuotaPeak : [2] 0x13068 +0x1b8 CommitCharge : 0x49d +0x1c0 QuotaBlock : 0xfffffa80`1aa2e840 _EPROCESS_QUOTA_BLOCK +0x1c8 CpuQuotaBlock : (null) +0x1d0 PeakVirtualSize : 0x5fc5000 +0x1d8 VirtualSize : 0x3fa2000 +0x1e0 SessionProcessLinks : _LIST_ENTRY [ 0xfffffa80`1ab84d10 - 0xfffffa80`1b0add10 ] +0x1f0 DebugPort : (null) +0x1f8 ExceptionPortData : 0xfffffa80`1a524e60 Void +0x1f8 ExceptionPortValue : 0xfffffa80`1a524e60 +0x1f8 ExceptionPortState : 0y000 +0x200 ObjectTable : 0xfffff8a0`01b11ab0 _HANDLE_TABLE +0x208 Token : _EX_FAST_REF +0x210 WorkingSetPage : 0x784c2 +0x218 AddressCreationLock : _EX_PUSH_LOCK +0x220 RotateInProgress : (null) +0x228 ForkInProgress : (null) +0x230 HardwareTrigger : 0 +0x238 PhysicalVadRoot : (null) +0x240 CloneRoot : (null) +0x248 NumberOfPrivatePages : 0x35d +0x250 NumberOfLockedPages : 0 +0x258 Win32Process : 0xfffff900`c1e42ce0 Void +0x260 Job : (null) +0x268 SectionObject : 0xfffff8a0`01b1fab0 Void +0x270 SectionBaseAddress : 0x00000000`ff830000 Void +0x278 Cookie : 0x87a6caf0 +0x27c UmsScheduledThreads : 0 +0x280 WorkingSetWatch : (null) +0x288 Win32WindowStation : 0x00000000`00000134 Void +0x290 InheritedFromUniqueProcessId : 0x00000000`0000022c Void +0x298 LdtInformation : (null) +0x2a0 Spare : (null) +0x2a8 ConsoleHostProcess : 0 +0x2b0 DeviceMap : 0xfffff8a0`00d8ca10 Void +0x2b8 EtwDataSource : 0xfffffa80`1ad8e290 Void +0x2c0 FreeTebHint : 0x000007ff`fffdc000 Void +0x2c8 FreeUmsTebHint : 0x00000001`00000000 Void +0x2d0 PageDirectoryPte : _HARDWARE_PTE +0x2d0 Filler : 0 +0x2d8 Session : 0xfffff880`04630000 Void +0x2e0 ImageFileName : [15] "svchost.exe" +0x2ef PriorityClass : 0x2 '' +0x2f0 JobLinks : _LIST_ENTRY [ 0x00000000`00000000 - 0x00000000`00000000 ] +0x300 LockedPagesList : (null) +0x308 ThreadListHead : _LIST_ENTRY [ 0xfffffa80`1b158a60 - 0xfffffa80`19704480 ] +0x318 SecurityPort : (null) +0x320 Wow64Process : (null) +0x328 ActiveThreads : 4 +0x32c ImagePathHash : 0xf5dbefc5 +0x330 DefaultHardErrorProcessing : 0 +0x334 LastThreadExitStatus : 0n0 +0x338 Peb : 0x000007ff`fffd7000 _PEB +0x340 PrefetchTrace : _EX_FAST_REF +0x348 ReadOperationCount : _LARGE_INTEGER 0x23 +0x350 WriteOperationCount : _LARGE_INTEGER 0x44 +0x358 OtherOperationCount : _LARGE_INTEGER 0x1fd4 +0x360 ReadTransferCount : _LARGE_INTEGER 0xa6d6a +0x368 WriteTransferCount : _LARGE_INTEGER 0x381e4 +0x370 OtherTransferCount : _LARGE_INTEGER 0x45269 +0x378 CommitChargeLimit : 0 +0x380 CommitChargePeak : 0x918 +0x388 AweInfo : (null) +0x390 SeAuditProcessCreationInfo : _SE_AUDIT_PROCESS_CREATION_INFO +0x398 Vm : _MMSUPPORT +0x420 MmProcessLinks : _LIST_ENTRY [ 0xfffffa80`1ab5df50 - 0xfffffa80`1b0adf50 ] +0x430 HighestUserAddress : 0x000007ff`ffff0000 Void +0x438 ModifiedPageCount : 0xbf +0x43c Flags2 : 0xd000 +0x43c JobNotReallyActive : 0y0 +0x43c AccountingFolded : 0y0 +0x43c NewProcessReported : 0y0 +0x43c ExitProcessReported : 0y0 +0x43c ReportCommitChanges : 0y0 +0x43c LastReportMemory : 0y0 +0x43c ReportPhysicalPageChanges : 0y0 +0x43c HandleTableRundown : 0y0 +0x43c NeedsHandleRundown : 0y0 +0x43c RefTraceEnabled : 0y0 +0x43c NumaAware : 0y0 +0x43c ProtectedProcess : 0y0 +0x43c DefaultPagePriority : 0y101 +0x43c PrimaryTokenFrozen : 0y1 +0x43c ProcessVerifierTarget : 0y0 +0x43c StackRandomizationDisabled : 0y0 +0x43c AffinityPermanent : 0y0 +0x43c AffinityUpdateEnable : 0y0 +0x43c PropagateNode : 0y0 +0x43c ExplicitAffinity : 0y0 +0x440 Flags : 0x144d0801 +0x440 CreateReported : 0y1 +0x440 NoDebugInherit : 0y0 +0x440 ProcessExiting : 0y0 +0x440 ProcessDelete : 0y0 +0x440 Wow64SplitPages : 0y0 +0x440 VmDeleted : 0y0 +0x440 OutswapEnabled : 0y0 +0x440 Outswapped : 0y0 +0x440 ForkFailed : 0y0 +0x440 Wow64VaSpace4Gb : 0y0 +0x440 AddressSpaceInitialized : 0y10 +0x440 SetTimerResolution : 0y0 +0x440 BreakOnTermination : 0y0 +0x440 DeprioritizeViews : 0y0 +0x440 WriteWatch : 0y0 +0x440 ProcessInSession : 0y1 +0x440 OverrideAddressSpace : 0y0 +0x440 HasAddressSpace : 0y1 +0x440 LaunchPrefetched : 0y1 +0x440 InjectInpageErrors : 0y0 +0x440 VmTopDown : 0y0 +0x440 ImageNotifyDone : 0y1 +0x440 PdeUpdateNeeded : 0y0 +0x440 VdmAllowed : 0y0 +0x440 CrossSessionCreate : 0y0 +0x440 ProcessInserted : 0y1 +0x440 DefaultIoPriority : 0y010 +0x440 ProcessSelfDelete : 0y0 +0x440 SetTimerResolutionLink : 0y0 +0x444 ExitStatus : 0n259 +0x448 VadRoot : _MM_AVL_TABLE +0x488 AlpcContext : _ALPC_PROCESS_CONTEXT +0x4a8 TimerResolutionLink : _LIST_ENTRY [ 0x00000000`00000000 - 0x00000000`00000000 ] +0x4b8 RequestedTimerResolution : 0 +0x4bc ActiveThreadsHighWatermark : 0xc +0x4c0 SmallestTimerResolution : 0 +0x4c8 TimerResolutionStackRecord : (null) eprocess+0x448 VadRoot 1: kd> dt _MM_AVL_TABLE 0xfffffa801b104b30+0x448 nt!_MM_AVL_TABLE +0x000 BalancedRoot : _MMADDRESS_NODE +0x028 DepthOfTree : 0y01000 (0x8) +0x028 Unused : 0y000 +0x028 NumberGenericTableElements : 0y00000000000000000000000000000000000000000000000001110000 (0x70) +0x030 NodeHint : 0xfffffa80`1b158e20 Void +0x038 NodeFreeHint : (null) eprocess->VadRoot->BlanceRoot 有一個右節點 1: kd> dt _MMADDRESS_NODE 0xfffffa801b104b30+0x448 nt!_MMADDRESS_NODE +0x000 u1 : <unnamed-tag> +0x008 LeftChild : (null) +0x010 RightChild : 0xfffffa80`1b158e20 _MMADDRESS_NODE +0x018 StartingVpn : 0 +0x020 EndingVpn : 0 看下這個節點 1: kd> dt _MMVAD 0xfffffa80`1b158e20 nt!_MMVAD +0x000 u1 : <unnamed-tag> +0x008 LeftChild : 0xfffffa80`1b167680 _MMVAD +0x010 RightChild : 0xfffffa80`1b157da0 _MMVAD +0x018 StartingVpn : 0x7ffe0 +0x020 EndingVpn : 0x7ffef +0x028 u : <unnamed-tag> +0x030 PushLock : _EX_PUSH_LOCK +0x038 u5 : <unnamed-tag> +0x040 u2 : <unnamed-tag> +0x048 Subsection : (null) +0x048 MappedSubsection : (null) +0x050 FirstPrototypePte : (null) +0x058 LastContiguousPte : (null) +0x060 ViewLinks : _LIST_ENTRY [ 0x00000000`00000000 - 0x00000000`00000000 ] +0x070 VadsProcess : (null) VadsProcess 是空的 說明這個不是正確的 繼續看下一個右節點 VadsProcess是一個有效值 說明是一個模組 1: kd> dt 0xfffffa80`1b157da0 _MMVAD nt!_MMVAD +0x000 u1 : <unnamed-tag> +0x008 LeftChild : 0xfffffa80`1b15ada0 _MMVAD +0x010 RightChild : 0xfffffa80`1b163ad0 _MMVAD +0x018 StartingVpn : 0x7fefdac0 +0x020 EndingVpn : 0x7fefdb2a +0x028 u : <unnamed-tag> +0x030 PushLock : _EX_PUSH_LOCK +0x038 u5 : <unnamed-tag> +0x040 u2 : <unnamed-tag> +0x048 Subsection : 0xfffffa80`19c1e330 _SUBSECTION +0x048 MappedSubsection : 0xfffffa80`19c1e330 _MSUBSECTION +0x050 FirstPrototypePte : 0xfffff8a0`004b9948 _MMPTE +0x058 LastContiguousPte : 0xffffffff`fffffffc _MMPTE +0x060 ViewLinks : _LIST_ENTRY [ 0xfffffa80`1b0db920 - 0xfffffa80`1b2dd450 ] +0x070 VadsProcess : 0xfffffa80`1b104b31 _EPROCESS 看一下Subsection 1: kd> dt 0xfffffa80`19c1e330 _SUBSECTION nt!_SUBSECTION +0x000 ControlArea : 0xfffffa80`19c1e2b0 _CONTROL_AREA +0x008 SubsectionBase : 0xfffff8a0`004b9948 _MMPTE +0x010 NextSubsection : 0xfffffa80`19c1e368 _SUBSECTION +0x018 PtesInSubsection : 1 +0x020 UnusedPtes : 0 +0x020 GlobalPerSessionHead : (null) +0x028 u : <unnamed-tag> +0x02c StartingSector : 0 +0x030 NumberOfFullSectors : 2 再看下ControlArea 1: kd> dt 0xfffffa80`19c1e2b0 _CONTROL_AREA nt!_CONTROL_AREA +0x000 Segment : 0xfffff8a0`004b9900 _SEGMENT +0x008 DereferenceList : _LIST_ENTRY [ 0x00000000`00000000 - 0x00000000`00000000 ] +0x018 NumberOfSectionReferences : 1 +0x020 NumberOfPfnReferences : 0x69 +0x028 NumberOfMappedViews : 0x23 +0x030 NumberOfUserReferences : 0x24 +0x038 u : <unnamed-tag> +0x03c FlushInProgressCount : 0 +0x040 FilePointer : _EX_FAST_REF +0x048 ControlAreaLock : 0n0 +0x04c ModifiedWriteCount : 0 +0x04c StartingFrame : 0 +0x050 WaitingForDeletion : (null) +0x058 u2 : <unnamed-tag> +0x068 LockedPages : 0n1 +0x070 ViewList : _LIST_ENTRY [ 0xfffffa80`1a93e420 - 0xfffffa80`1a31f5f0 ] 再看FilePointer 1: kd> dt _EX_FAST_REF 0xfffffa80`19c1e2b0+0x40 nt!_EX_FAST_REF +0x000 Object : 0xfffffa80`19c1df27 Void +0x000 RefCnt : 0y0111 +0x000 Value : 0xfffffa80`19c1df27 去除低4位就是真正的FileObject,這裡就可以看到模組名了 1: kd> dt _file_object 0xfffffa80`19c1df20 nt!_FILE_OBJECT +0x000 Type : 0n5 +0x002 Size : 0n216 +0x008 DeviceObject : 0xfffffa80`192df480 _DEVICE_OBJECT +0x010 Vpb : 0xfffffa80`192dd2b0 _VPB +0x018 FsContext : 0xfffff8a0`04008890 Void +0x020 FsContext2 : 0xfffff8a0`04008a80 Void +0x028 SectionObjectPointer : 0xfffffa80`19c1de18 _SECTION_OBJECT_POINTERS +0x030 PrivateCacheMap : (null) +0x038 FinalStatus : 0n0 +0x040 RelatedFileObject : 0xfffffa80`193fc930 _FILE_OBJECT +0x048 LockOperation : 0 '' +0x049 DeletePending : 0 '' +0x04a ReadAccess : 0x1 '' +0x04b WriteAccess : 0 '' +0x04c DeleteAccess : 0 '' +0x04d SharedRead : 0x1 '' +0x04e SharedWrite : 0 '' +0x04f SharedDelete : 0x1 '' +0x050 Flags : 0x44042 +0x058 FileName : _UNICODE_STRING "\Windows\System32\KernelBase.dll" +0x068 CurrentByteOffset : _LARGE_INTEGER 0x0 +0x070 Waiters : 0 +0x074 Busy : 0 +0x078 LastLock : (null) +0x080 Lock : _KEVENT +0x098 Event : _KEVENT +0x0b0 CompletionContext : (null) +0x0b8 IrpListLock : 0 +0x0c0 IrpList : _LIST_ENTRY [ 0xfffffa80`19c1dfe0 - 0xfffffa80`19c1dfe0 ] +0x0d0 FileObjectExtension : (null) 在下Segment,有基址 如果要隱藏的話這個地方要置0 1: kd> dt 0xfffff8a0`004b9900 _SEGMENT nt!_SEGMENT +0x000 ControlArea : 0xfffffa80`19c1e2b0 _CONTROL_AREA +0x008 TotalNumberOfPtes : 0x6b +0x00c SegmentFlags : _SEGMENT_FLAGS +0x010 NumberOfCommittedPages : 0 +0x018 SizeOfSegment : 0x6b000 +0x020 ExtendInfo : 0x000007fe`fdac0000 _MMEXTEND_INFO +0x020 BasedAddress : 0x000007fe`fdac0000 Void +0x028 SegmentLock : _EX_PUSH_LOCK +0x030 u1 : <unnamed-tag> +0x038 u2 : <unnamed-tag> +0x040 PrototypePte : 0xfffff8a0`004b9948 _MMPTE +0x048 ThePtes : [1] _MMPTE
程式碼就很簡單了 ,就是遍歷二叉樹.自己寫去吧