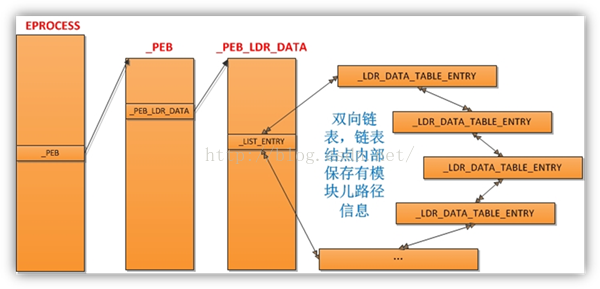
PEB遍歷程序載入模組
阿新 • • 發佈:2019-02-03
按照圖片的步驟來
首先找到EPROCESS
以CMD.exe為例子
PROCESS 85fa2b38 SessionId: 0 Cid: 0fc8 Peb: 7ffda000 ParentCid: 05f8
DirBase: 0f3c03a0 ObjectTable: e1fa93c8 HandleCount: 34.
Image: cmd.exe
可以看到peb為 7ffda000
進入程序空間
檢視PEBkd> .process 85fa2b38 Implicit process is now 85fa2b38 WARNING: .cache forcedecodeuser is not enabled
kd> dt _PEB 7ffda000 nt!_PEB +0x000 InheritedAddressSpace : 0 '' +0x001 ReadImageFileExecOptions : 0 '' +0x002 BeingDebugged : 0 '' +0x003 SpareBool : 0 '' +0x004 Mutant : 0xffffffff Void +0x008 ImageBaseAddress : 0x4ad00000 Void +0x00c Ldr : 0x00251e90 _PEB_LDR_DATA +0x010 ProcessParameters : 0x00020000 _RTL_USER_PROCESS_PARAMETERS +0x014 SubSystemData : (null) +0x018 ProcessHeap : 0x00150000 Void +0x01c FastPebLock : 0x7c99d600 _RTL_CRITICAL_SECTION +0x020 FastPebLockRoutine : 0x7c921000 Void +0x024 FastPebUnlockRoutine : 0x7c9210e0 Void +0x028 EnvironmentUpdateCount : 2 +0x02c KernelCallbackTable : 0x77d12970 Void +0x030 SystemReserved : [1] 0 +0x034 AtlThunkSListPtr32 : 0 +0x038 FreeList : (null) +0x03c TlsExpansionCounter : 0 +0x040 TlsBitmap : 0x7c99d5c0 Void +0x044 TlsBitmapBits : [2] 0xffff +0x04c ReadOnlySharedMemoryBase : 0x7f6f0000 Void +0x050 ReadOnlySharedMemoryHeap : 0x7f6f0000 Void +0x054 ReadOnlyStaticServerData : 0x7f6f0688 -> ???? +0x058 AnsiCodePageData : 0x7ffa0000 Void +0x05c OemCodePageData : 0x7ffa0000 Void +0x060 UnicodeCaseTableData : 0x7ffd1000 Void +0x064 NumberOfProcessors : 1 +0x068 NtGlobalFlag : 0 +0x070 CriticalSectionTimeout : _LARGE_INTEGER 0xffffe86d`079b8000 +0x078 HeapSegmentReserve : 0x100000 +0x07c HeapSegmentCommit : 0x2000 +0x080 HeapDeCommitTotalFreeThreshold : 0x10000 +0x084 HeapDeCommitFreeBlockThreshold : 0x1000 +0x088 NumberOfHeaps : 9 +0x08c MaximumNumberOfHeaps : 0x10 +0x090 ProcessHeaps : 0x7c99cfc0 -> 0x00150000 Void +0x094 GdiSharedHandleTable : 0x00570000 Void +0x098 ProcessStarterHelper : (null) +0x09c GdiDCAttributeList : 0x14 +0x0a0 LoaderLock : 0x7c99b178 Void +0x0a4 OSMajorVersion : 5 +0x0a8 OSMinorVersion : 1 +0x0ac OSBuildNumber : 0xa28 +0x0ae OSCSDVersion : 0x300 +0x0b0 OSPlatformId : 2 +0x0b4 ImageSubsystem : 3 +0x0b8 ImageSubsystemMajorVersion : 4 +0x0bc ImageSubsystemMinorVersion : 0 +0x0c0 ImageProcessAffinityMask : 0 +0x0c4 GdiHandleBuffer : [34] 0 +0x14c PostProcessInitRoutine : (null) +0x150 TlsExpansionBitmap : 0x7c99d5b8 Void +0x154 TlsExpansionBitmapBits : [32] 0 +0x1d4 SessionId : 0 +0x1d8 AppCompatFlags : _ULARGE_INTEGER 0x0 +0x1e0 AppCompatFlagsUser : _ULARGE_INTEGER 0x0 +0x1e8 pShimData : (null) +0x1ec AppCompatInfo : (null) +0x1f0 CSDVersion : _UNICODE_STRING "--- memory read error at address 0x7f6f06c2 ---" +0x1f8 ActivationContextData : (null) +0x1fc ProcessAssemblyStorageMap : (null) +0x200 SystemDefaultActivationContextData : 0x00140000 Void +0x204 SystemAssemblyStorageMap : (null) +0x208 MinimumStackCommit : 0
檢視
_PEB_LDR_DATAkd> dt _PEB_LDR_DATA 0x00251e90 nt!_PEB_LDR_DATA +0x000 Length : 0x28 +0x004 Initialized : 0x1 '' +0x008 SsHandle : (null) +0x00c InLoadOrderModuleList : _LIST_ENTRY [ 0x251ec0 - 0x252ee0 ] +0x014 InMemoryOrderModuleList : _LIST_ENTRY [ 0x251ec8 - 0x252ee8 ] +0x01c InInitializationOrderModuleList : _LIST_ENTRY [ 0x251f28 - 0x252ef0 ] +0x024 EntryInProgress : (null)
檢視_LDR_DATA_TABLE_ENTRY
kd> dt _LDR_DATA_TABLE_ENTRY 0x251ec0
nt!_LDR_DATA_TABLE_ENTRY
+0x000 InLoadOrderLinks : _LIST_ENTRY [ 0x251f18 - 0x251e9c ]
+0x008 InMemoryOrderLinks : _LIST_ENTRY [ 0x251f20 - 0x251ea4 ]
+0x010 InInitializationOrderLinks : _LIST_ENTRY [ 0x0 - 0x0 ]
+0x018 DllBase : 0x4ad00000 Void
+0x01c EntryPoint : 0x4ad05046 Void
+0x020 SizeOfImage : 0x75000
+0x024 FullDllName : _UNICODE_STRING "???????????????????????????"
+0x02c BaseDllName : _UNICODE_STRING "???????"
+0x034 Flags : 0x5000
+0x038 LoadCount : 0xffff
+0x03a TlsIndex : 0
+0x03c HashLinks : _LIST_ENTRY [ 0x252dd4 - 0x7c99b270 ]
+0x03c SectionPointer : 0x00252dd4 Void
+0x040 CheckSum : 0x7c99b270
+0x044 TimeDateStamp : 0x48025baf
+0x044 LoadedImports : 0x48025baf Void
+0x048 EntryPointActivationContext : (null)
+0x04c PatchInformation : (null) 可以看到我們的FullDLLName雖然顯示不出但是我們可以驗證下一個0x251f18
kd> dt _LDR_DATA_TABLE_ENTRY 0x251f18
nt!_LDR_DATA_TABLE_ENTRY
+0x000 InLoadOrderLinks : _LIST_ENTRY [ <span style="color:#ff0000;">0x251fc0</span> - 0x251ec0 ]
+0x008 InMemoryOrderLinks : _LIST_ENTRY [ 0x251fc8 - 0x251ec8 ]
+0x010 InInitializationOrderLinks : _LIST_ENTRY [ 0x251fd0 - 0x251eac ]
+0x018 DllBase : 0x7c920000 Void
+0x01c EntryPoint : 0x7c932c28 Void
+0x020 SizeOfImage : 0x93000
+0x024 FullDllName : _UNICODE_STRING "C:\WINDOWS\system32\ntdll.dll"
+0x02c BaseDllName : _UNICODE_STRING "ntdll.dll"
+0x034 Flags : 0x80084004
+0x038 LoadCount : 0xffff
+0x03a TlsIndex : 0
+0x03c HashLinks : _LIST_ENTRY [ 0x7c99b2c8 - 0x7c99b2c8 ]
+0x03c SectionPointer : 0x7c99b2c8 Void
+0x040 CheckSum : 0x7c99b2c8
+0x044 TimeDateStamp : 0x4802bdc5
+0x044 LoadedImports : 0x4802bdc5 Void
+0x048 EntryPointActivationContext : (null)
+0x04c PatchInformation : (null)
然後再通過
+0x000 InLoadOrderLinks : _LIST_ENTRY [ <span style="color:#ff0000;">0x251fc0</span> - 0x251ec0 ]直到遍歷回最初的模組就是的了