spring boot 開發—第八篇整合OAuth2保證api介面安全
1、 OAuth 概念
OAuth 是一個開放標準,允許使用者讓第三方應用訪問該使用者在某一網站上儲存的私密的資源(如照片,視訊,聯絡人列表),而不需要將使用者名稱和密碼提供給第三方應用。OAuth允許使用者提供一個令牌,而不是使用者名稱和密碼來訪問他們存放在特定服務提供者的資料。每一個令牌授權一個特定的網站在特定的時段內訪問特定的資源。這樣,OAuth讓使用者可以授權第三方網站訪問他們儲存在另外服務提供者的某些特定資訊,而非所有內容。
2、OAuth 2.0 認證流程
第一步:得到授權碼 code
首先直接跳轉至使用者授權地址,即圖示 Request User Url ,提示使用者進行登入,並給予相關資源授權,得到唯一的 Auth code ,這裡注意的是 code 只有 10 分鐘的有效期,對於安全考慮,相對於 OAuth 1.0 省了一步獲取臨時的 Token ,並且有效期也進行了控制,比 1.0 認證簡化了很多,並安全一些;
第二步:獲取 access token
得到授權 code 後,就是請求 access token ,通過圖示 Request access url ,生成得到資料 Token ;
第三步:通過 access token, 獲取 OpenID
通過 Access Token 請求 OpenID , OpenID 是使用者在此平臺的唯一標識,通過圖示 Request info url 請求,然後得到 OpenID ;
第四步:通過 access token 及 OpenID 呼叫 API,獲取使用者授權資訊
通過第二步得到的資料 Token 、第三步得到的 OpenID 及相關 API ,進行請求,獲取使用者授權資源資訊。
3、OAuth 授權模式
OAuth2.0 定義了 四種授權模式。分別為:
- 授權碼模式
- 簡化模式
- 密碼模式
- 客戶端模式
4、oauth2 例項
可以分為簡易的分為三個步驟
- 配置資源伺服器
- 配置認證伺服器
- 配置spring security
4.1、構建工程
pom檔案新增oauth2依賴
<dependency> <groupId>org.springframework.boot</groupId> <artifactId>spring-boot-starter-security</artifactId> </dependency> <dependency> <groupId>org.springframework.security.oauth</groupId> <artifactId>spring-security-oauth2</artifactId> </dependency>
4.2、配置資源伺服器
@EnableResourceServer註解來開啟資源伺服器
package com.vesus.springbootoauth2.config;
import org.slf4j.Logger;
import org.slf4j.LoggerFactory;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.config.annotation.web.builders.HttpSecurity;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableResourceServer;
import org.springframework.security.oauth2.config.annotation.web.configuration.ResourceServerConfigurerAdapter;
@Configuration
@EnableResourceServer
public class ResourceServerConfiguration extends ResourceServerConfigurerAdapter {
private Logger logger = LoggerFactory.getLogger(ResourceServerConfiguration.class);
@Autowired
private CustomAuthenticationEntryPoint customAuthenticationEntryPoint ;
@Bean
public CustomLogoutSuccessHandler customLogoutSuccessHandler(){
return new CustomLogoutSuccessHandler();
} ;
@Override
public void configure(HttpSecurity http) throws Exception {
logger.info("=========================111111111=========");
http.exceptionHandling()
.authenticationEntryPoint(customAuthenticationEntryPoint)
.and()
.logout()
.logoutUrl("/oauth/logout")
.logoutSuccessHandler(customLogoutSuccessHandler())
.and()
.authorizeRequests()
.antMatchers("/hello/").permitAll()
.antMatchers("/secure/**").authenticated();
}
}
4.3、自定義401錯誤碼內容
package com.vesus.springbootoauth2.config;
import org.slf4j.Logger;
import org.slf4j.LoggerFactory;
import org.springframework.security.core.AuthenticationException;
import org.springframework.security.web.AuthenticationEntryPoint;
import org.springframework.stereotype.Component;
import javax.servlet.ServletException;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
@Component
public class CustomAuthenticationEntryPoint implements AuthenticationEntryPoint {
private final Logger log = LoggerFactory.getLogger(CustomAuthenticationEntryPoint.class);
@Override
public void commence(HttpServletRequest request, HttpServletResponse response, AuthenticationException authException) throws IOException, ServletException {
log.info("Pre-authenticated entry point called. Rejecting access");
response.sendError(HttpServletResponse.SC_UNAUTHORIZED,"Access Denied");
}
}
4.4、定義登出控制
退出系統時需要訪問SpringSecrutiy的logout方法來清空對應的token資訊
package com.vesus.springbootoauth2.config;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.security.core.Authentication;
import org.springframework.security.oauth2.common.OAuth2AccessToken;
import org.springframework.security.oauth2.provider.token.TokenStore;
import org.springframework.security.web.authentication.AbstractAuthenticationTargetUrlRequestHandler;
import org.springframework.security.web.authentication.logout.LogoutSuccessHandler;
import javax.servlet.ServletException;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import java.io.IOException;
public class CustomLogoutSuccessHandler extends AbstractAuthenticationTargetUrlRequestHandler implements LogoutSuccessHandler {
private static final String BEARER_AUTHENTICATION = "Bearer ";
private static final String HEADER_AUTHORIZATION = "authorization";
@Autowired
private TokenStore tokenStore ;
@Override
public void onLogoutSuccess(HttpServletRequest request, HttpServletResponse response, Authentication authentication) throws IOException, ServletException {
String token = request.getHeader(HEADER_AUTHORIZATION);
if (token!=null&&token.startsWith(BEARER_AUTHENTICATION)){
OAuth2AccessToken oAuth2AccessToken = tokenStore.readAccessToken(token.split(" ")[0]);
if (oAuth2AccessToken!=null){
tokenStore.removeAccessToken(oAuth2AccessToken);
}
}
response.setStatus(HttpServletResponse.SC_OK);
}
}
4.5、配置OAuth2驗證伺服器
@EnableAuthorizationServer註解開啟驗證伺服器
package com.vesus.springbootoauth2.config;
import org.slf4j.Logger;
import org.slf4j.LoggerFactory;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.beans.factory.annotation.Qualifier;
import org.springframework.boot.bind.RelaxedPropertyResolver;
import org.springframework.context.EnvironmentAware;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.core.env.Environment;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.oauth2.config.annotation.configurers.ClientDetailsServiceConfigurer;
import org.springframework.security.oauth2.config.annotation.web.configuration.AuthorizationServerConfigurerAdapter;
import org.springframework.security.oauth2.config.annotation.web.configuration.EnableAuthorizationServer;
import org.springframework.security.oauth2.config.annotation.web.configurers.AuthorizationServerEndpointsConfigurer;
import org.springframework.security.oauth2.provider.token.TokenStore;
import org.springframework.security.oauth2.provider.token.store.JdbcTokenStore;
import javax.sql.DataSource;
@Configuration
@EnableAuthorizationServer
public class AuthorizationServerConfiguration extends AuthorizationServerConfigurerAdapter implements EnvironmentAware {
private Logger logger = LoggerFactory.getLogger(AuthorizationServerConfiguration.class);
private static final String ENV_OAUTH = "authentication.oauth.";
private static final String PROP_CLIENTID = "clientid";
private static final String PROP_SECRET = "secret";
private static final String PROP_TOKEN_VALIDITY_SECONDS = "tokenValidityInSeconds";
private RelaxedPropertyResolver propertyResolver ;
@Autowired
private DataSource dataSource ;
@Bean
public TokenStore tokenStore(){
//這個是基於JDBC的實現,令牌(Access Token)會儲存到資料庫
return new JdbcTokenStore(dataSource);
}
@Autowired
@Qualifier("authenticationManagerBean")//認證方式
private AuthenticationManager authenticationManager ;
@Override
public void configure(AuthorizationServerEndpointsConfigurer endpoints) throws Exception {
endpoints.tokenStore(tokenStore())
.authenticationManager(authenticationManager) ;
}
public void configure(ClientDetailsServiceConfigurer clients) throws Exception {
clients.inMemory() // 使用in-memory儲存
.withClient(propertyResolver.getProperty(PROP_CLIENTID))//client_id用來標識客戶的Id
.scopes("read", "write") //允許授權範圍
.authorities("ROLE_ADMIN","ROLE_USER")//客戶端可以使用的許可權
.authorizedGrantTypes("password", "refresh_token")//允許授權型別
.secret(propertyResolver.getProperty(PROP_SECRET))//secret客戶端安全碼
.accessTokenValiditySeconds(propertyResolver.getProperty(PROP_TOKEN_VALIDITY_SECONDS, Integer.class, 1800));
}
@Override
public void setEnvironment(Environment environment) {
//獲取到字首是"authentication.oauth." 的屬性列表值.
this.propertyResolver = new RelaxedPropertyResolver(environment, ENV_OAUTH);
}
}
4.6、安全配置
package com.vesus.springbootoauth2.config;
import com.vesus.springbootoauth2.service.impl.CustomUserService;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import org.springframework.security.access.expression.method.MethodSecurityExpressionHandler;
import org.springframework.security.authentication.AuthenticationManager;
import org.springframework.security.config.annotation.authentication.builders.AuthenticationManagerBuilder;
import org.springframework.security.config.annotation.method.configuration.EnableGlobalMethodSecurity;
import org.springframework.security.config.annotation.method.configuration.GlobalMethodSecurityConfiguration;
import org.springframework.security.config.annotation.web.builders.WebSecurity;
import org.springframework.security.config.annotation.web.configuration.EnableWebSecurity;
import org.springframework.security.config.annotation.web.configuration.WebSecurityConfigurerAdapter;
import org.springframework.security.core.userdetails.UserDetailsService;
import org.springframework.security.oauth2.provider.expression.OAuth2MethodSecurityExpressionHandler;
@Configuration
@EnableWebSecurity
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
@Bean
UserDetailsService customUserService(){
return new CustomUserService();
}
//配置全域性設定
@Autowired
public void configureGlobal(AuthenticationManagerBuilder auth) throws Exception {
//設定UserDetailsService以及密碼規則
auth.userDetailsService(customUserService());
}
@Override
public void configure(WebSecurity web) throws Exception {
web.ignoring().antMatchers("/hello") ;
}
@Bean
public AuthenticationManager authenticationManagerBean() throws Exception {
return super.authenticationManagerBean() ;
}
//開啟全域性方法攔截
@EnableGlobalMethodSecurity(prePostEnabled = true, jsr250Enabled = true)
public static class GlobalSecurityConfiguration extends GlobalMethodSecurityConfiguration {
@Override
protected MethodSecurityExpressionHandler createExpressionHandler() {
return new OAuth2MethodSecurityExpressionHandler();
}
}
}
4.7、啟動
訪問localhost:8080/hello
hello
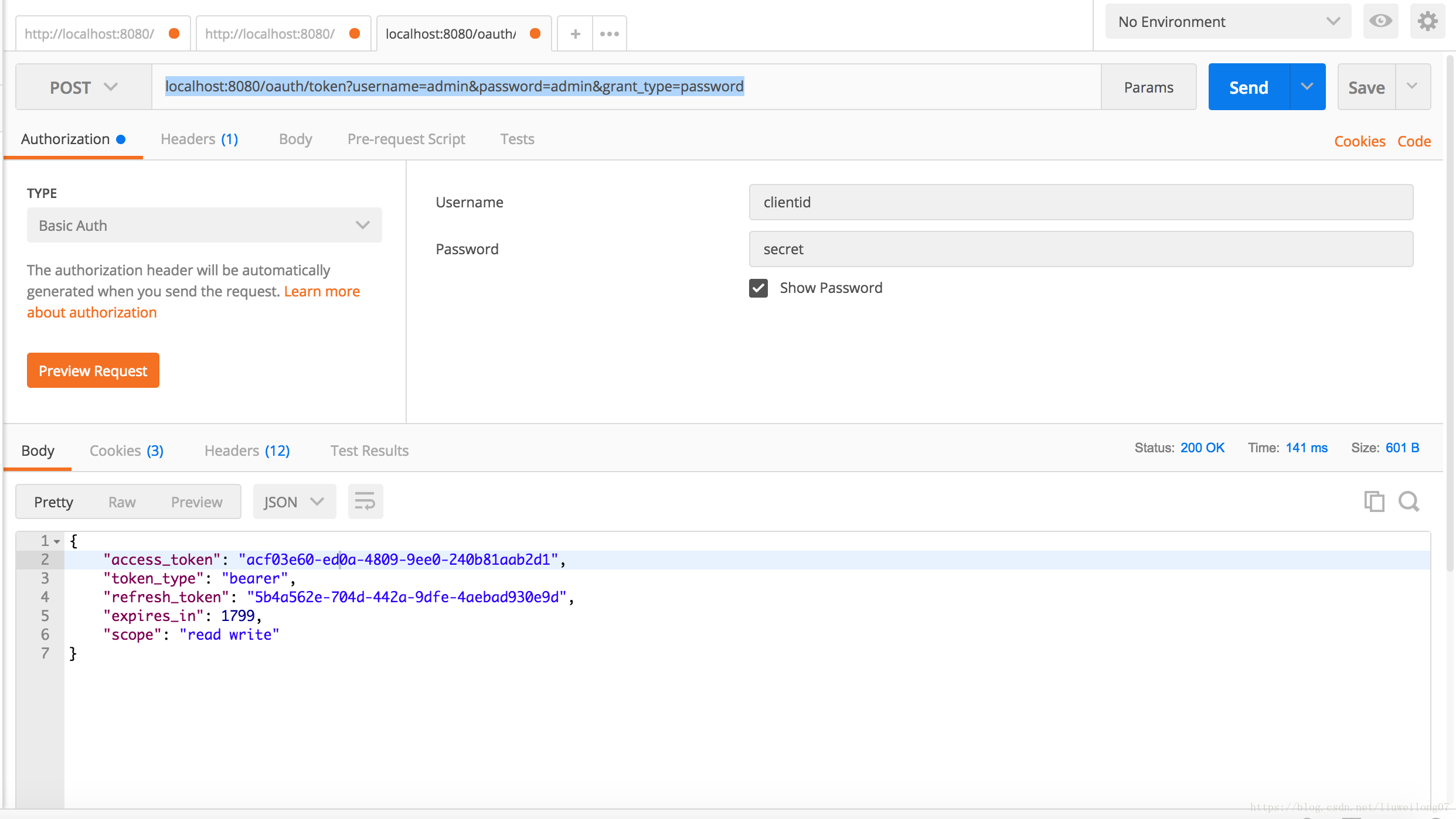
使用postman訪問localhost:8080/oauth/token?username=admin&password=admin&grant_type=password
{
"access_token": "acf03e60-ed0a-4809-9ee0-240b81aab2d1",
"token_type": "bearer",
"refresh_token": "5b4a562e-704d-442a-9dfe-4aebad930e9d",
"expires_in": 1799,
"scope": "read write"
}
login