kubernetes部署dashboard視覺化外掛
dashboard簡介
Kubernetes 大部分的操作都是通過命令列工具 kubectl 完成的,為了提供更豐富的使用者體驗,Kubernetes 還開發了一個基於 Web 的 Dashboard,使用者可以用 Kubernetes Dashboard 部署容器化的應用、監控應用的狀態、執行故障排查任務以及管理 Kubernetes 各種資源。
在 Kubernetes Dashboard 中可以檢視叢集中應用的執行狀態,也能夠建立和修改各種 Kubernetes 資源,比如 Deployment、Job、DaemonSet 等。使用者可以 Scale Up/Down Deployment、執行 Rolling Update、重啟某個 Pod 或者通過嚮導部署新的應用。Dashboard 能顯示叢集中各種資源的狀態以及日誌資訊。
官方參考連結:
https://kubernetes.io/docs/tasks/access-application-cluster/web-ui-dashboard/#deploying-the-dashboard-ui
kubernetes叢集準備
kubeadm部署3節點kubernetes1.13.0叢集(1master節點+2node節點),叢集部署參考:
https://blog.csdn.net/networken/article/details/84991940
部署dashboard
安裝dashboard
Kubernetes 預設沒有部署 Dashboard,可通過如下命令安裝:
kubectl create - 獲取kubernetes-dashboard.yaml檔案:
由於yml檔案中指定映象從google倉庫下載,這裡先下載yaml檔案,替換映象下載路徑從阿里雲映象倉庫下載:
[[email protected]-master ~]$wget https://raw.githubusercontent.com/kubernetes/dashboard/master/src/deploy/recommended/kubernetes- 然後執行以下命令部署dashboard服務:
[[email protected]-master ~]$ kubectl create -f kubernetes-dashboard.yaml
secret/kubernetes-dashboard-certs created
serviceaccount/kubernetes-dashboard created
role.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
rolebinding.rbac.authorization.k8s.io/kubernetes-dashboard-minimal created
deployment.apps/kubernetes-dashboard created
service/kubernetes-dashboard created
[[email protected]-master ~]$
Dashboard 會在 kube-system namespace 中建立自己的 Deployment 和 Service。
[[email protected]-master ~]$ kubectl get deployment kubernetes-dashboard --namespace=kube-system
NAME READY UP-TO-DATE AVAILABLE AGE
kubernetes-dashboard 1/1 1 1 21m
[[email protected]-master ~]$
[[email protected]-master ~]$ kubectl get service kubernetes-dashboard --namespace=kube-system
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes-dashboard NodePort 10.104.254.251 <none> 443:30001/TCP 21m
[[email protected]-master ~]$
檢視pod狀態執行正常:
[[email protected] ~]$ kubectl get pod --namespace=kube-system -o wide | grep kubernetes-dashboard
kubernetes-dashboard-847f8cb7b8-wrm4l 1/1 Running 0 19m 10.244.2.5 k8s-node2 <none> <none>
[[email protected] ~]$
因為 Service 是 ClusterIP 型別,為了便於本地訪問,我們可通過以下命令修改成 NodePort 型別,並指定埠為30001,修改後可以基於ip:30001的方式來訪問。
在檔案中的spec部分下新增type: NodePort和nodePort: 30001,新增位置如下所示:
[[email protected]-master ~]$ kubectl edit service kubernetes-dashboard --namespace=kube-system
......
spec:
clusterIP: 10.104.254.251
externalTrafficPolicy: Cluster
ports:
- port: 443
protocol: TCP
targetPort: 8443
nodePort: 30001
selector:
k8s-app: kubernetes-dashboard
sessionAffinity: None
type: NodePort
status:
loadBalancer: {}
儲存修改再次檢視service,此時修改已經生效,TYPE為NodePort,埠為30001。
[[email protected]-master ~]$ kubectl --namespace=kube-system get service kubernetes-dashboard
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes-dashboard NodePort 10.233.207.111 <none> 443:30001/TCP 3m22s
[[email protected]-master ~]$
通過瀏覽器訪問 Dashboard ,https://192.168.92.56:30001/,登入介面如下:
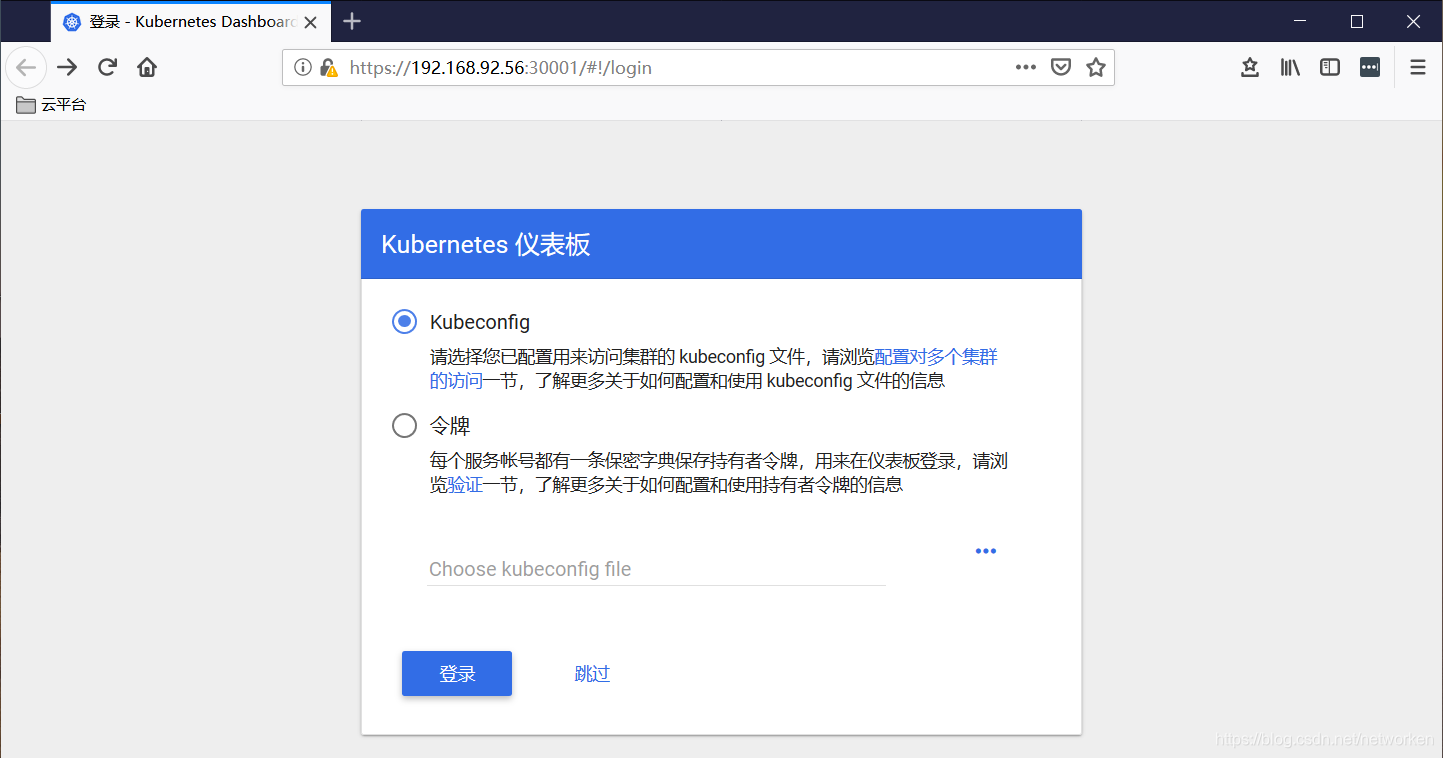
建立登入令牌
Dashboard 支援 Kubeconfig 和 Token 兩種認證方式,我們這裡選擇Token方式登入。
建立admin-user.yaml檔案,內容如下:
[[email protected]-master ~]$ vim admin-user.yaml
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
name: admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: admin
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin
namespace: kube-system
執行:kubectl create -f admin-user.yaml,並檢視service
[[email protected]-master ~]$ kubectl create -f admin-user.yaml
serviceaccount/admin created
clusterrolebinding.rbac.authorization.k8s.io/admin created
[[email protected]-master ~]$ kubectl describe serviceaccounts admin -n kube-system
Name: admin
Namespace: kube-system
Labels: k8s-app=kubernetes-dashboard
Annotations: <none>
Image pull secrets: <none>
Mountable secrets: admin-token-nngz2
Tokens: admin-token-nngz2
Events: <none>
[[email protected]-master ~]$
獲取token名稱後檢視token:
[[email protected]-master ~]$ kubectl describe secrets admin-token-nngz2 -n kube-system
Name: admin-token-nngz2
Namespace: kube-system
Labels: <none>
Annotations: kubernetes.io/service-account.name: admin
kubernetes.io/service-account.uid: 69c9d23c-fea1-11e8-b2e3-000c291c2 5f3
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1025 bytes
namespace: 11 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY 2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSI sImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi10b2tlbi1ubmd6M iIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiI sImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjY5YzlkMjNjL WZlYTEtMTFlOC1iMmUzLTAwMGMyOTFjMjVmMyIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJ lLXN5c3RlbTphZG1pbiJ9.kuQAF7LsA_80ql-4hGhyn7ScR77NmlU7hNUqxP-gYnZyiaWTznse7FA9uvwr 15Mmb2yO-_7McaCLER77VJkDalLV0kdwG6PG05c4vxT-7HBzg6TFch1jLHSx2QIso5LfKm4sz_Mm7agYT5 bFGBSWZKt5Lk6wITewx78QkIipdz3F7oqlRNE0abrk6BdX3RcIVwt--ooFGKnEzLtZ9epc8w0TceQLl2p- pbZj093Us44Xjc8P8_lnvmjwqfM8Y2ukdcGnJNTSu3u_zkUK_G8dsq9LdqJORkVh4gf29XONQcx-DD1NOw Yiektw0DlxEab8fwT8nqWqqsj4Ea1xtWfTCg
[[email protected]-master ~]$
複製最後一行token:後的內容,登入dashboard:
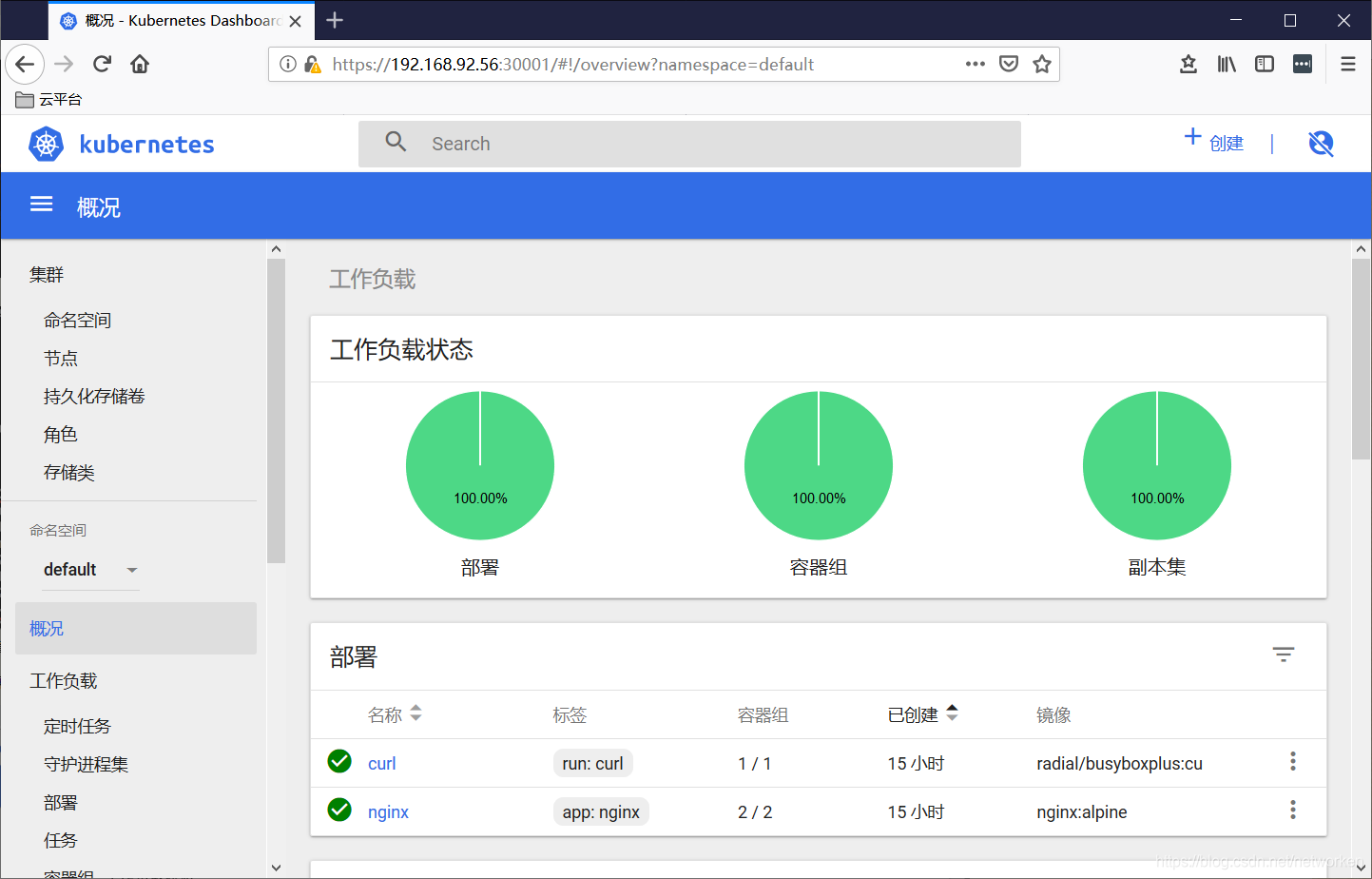
admin登入dashboard
為了簡化配置,我們也可以通過配置檔案 dashboard-admin.yaml 為 Dashboard 預設使用者賦予 admin 許可權。
[[email protected]-master ~]$ vim dashboard-admin.yaml
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1beta1
metadata:
name: kubernetes-dashboard
labels:
k8s-app: kubrnetes-dashboard
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard
namespace: kube-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
執行 kubectl apply 使之生效。
[[email protected]-master ~]$ kubectl apply -f dashboard-admin.yaml
clusterrolebinding.rbac.authorization.k8s.io/kubernetes-dashboard created
[[email protected]-master ~]$
現在直接點選登入頁面的 SKIP 也可以進入 Dashboard 。
