Fine-Grained Access Control for Amazon DynamoDB
I truly enjoy the process of putting blog posts together for new AWS services and features. Many features started out as specific requests from one of the hundreds of thousands of AWS users. With “customer obsession” as one of our core values, all of us on the AWS team do everything that we can to listen to our customers and to make sure that their feedback ends up in the Inbox of the right service team.
Amazon DynamoDB has become very popular with developers in a very short time. Many developers are using building mobile apps and online games using DynamoDB. Apps of this type can benefit from DynamoDB’s scalability, flexibility, and efficiency. These apps generally use a single table to store information for the entire user base, which can easily grow to the millions or tens of millions of users. This scenario requires the use of a proxy tier between the app and DynamoDB in order to handle authentication and authorization.
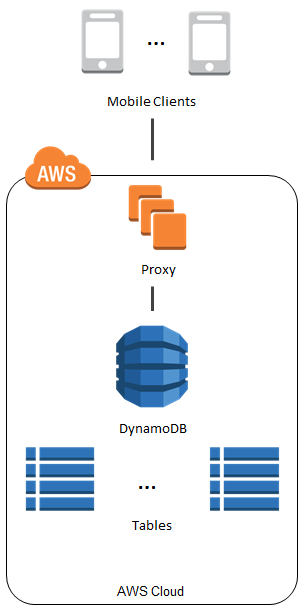
The proxy introduces additional latency and complexity, not to mention the added expense. We saw this proxy-based architecture frequently. In most cases the proxy did nothing more than regulate access to particular items and (occasionally) attributes.
Fine-Grained Access Control for DynamoDB
To make it easier for you to implement the use case that I described above, we are launching Fine-Grained Access Control for DynamoDB today. You can now use AWS Identity and Access Management (IAM) policies to regulate access to items and attributes stored in DynamoDB tables, without the need for a middle-tier proxy as illustrated above.
Here are some of the things that you can build using fine-grained access control:
- A mobile app that displays information for nearby airports, based on the user’s location. The app can access and display attributes such airline names, arrival times, and flight numbers. However, it cannot access or display pilot names or passenger counts.
- A mobile game which stores high scores for all users in a single table. Each user can update their own scores, but has no access to the other ones.
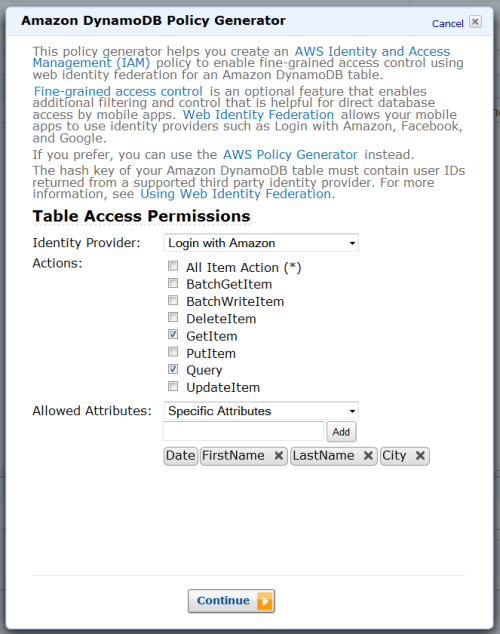
The IAM Condition element is used to implement fine-grained access control. You can use this element to allow or deny access to items and attributes based on the needs of your application. Here are your options:
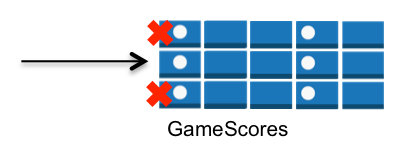
Horizontal – You can selectively hide or expose specific DynamoDB items in a particular table by matching on hash key values:
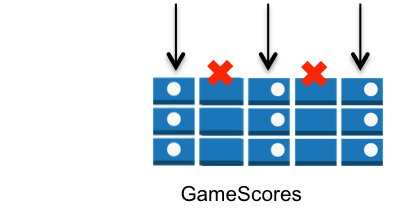
Vertical – You can selectively hide or expose specific attributes of all of the DynamoDB items in a particular table by matching on attribute names:
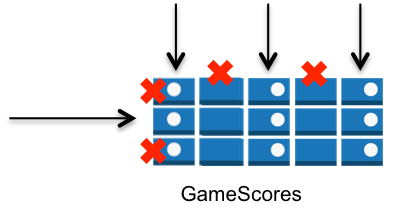
Combined – You can exercise horizontal and vertical control in the same policy:
You can combine these options with the IAM Action element to exercise even more control. For example, you can create read-only variants of the options described above by allowing only and Query in your policy.
Using Fine-Grained Access Control
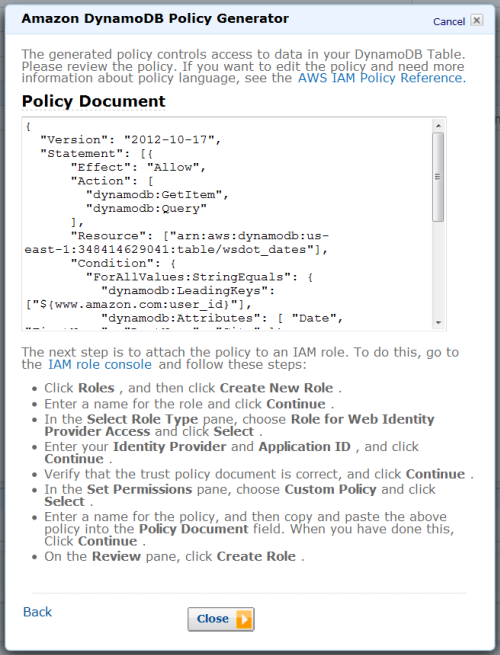
Visit the Fine-Grained Access Control section of the DynamoDB Developer Guide to learn how to create an access policy, create an IAM role, and assign your access policy to the role. We also have a collection of sample policies.
The trust policy of the role determines which identity providers are accepted (e.g. Login with Amazon, Facebook, or Google) and the access policy determines which AWS resources (e.g. the DynamoDB tables, items, and attributes) can be accessed.
Here is a very simple policy. Each authenticated user has read-only access to their own items in the GameScores table:
{ "Version": "2012-10-17", "Statement": [{ "Effect": "Allow", "Action": [ "dynamodb:GetItem", "dynamodb:BatchGetItem", "dynamodb:Query" ], "Resource": ["arn:aws:dynamodb:us-west-2:123456789012:dynamodb:table/GameScores"], "Condition": { "ForAllValues:StringEquals": { "dynamodb:LeadingKeys": ["${www.amazon.com:user_id}"] } } }] }
Your code will use the role to obtain temporary security credentials for DynamoDB by calling the AssumeRoleWithWebIdentity function of the AWS Security Token Service.
You can use the new DynamoDB Policy Generator to create your first policy. Go to the DynamoDB Console, select the table, and click the Access Control button:
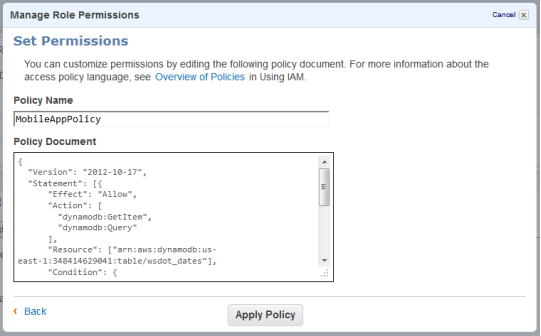
After you create it, head over to the IAM Console, create a role for Web Identity Provider access with no permissions, and then paste the policy into the role.
Watch and Learn
We have created a video tutorial to help you to get started with Fine-Grained Access Control for DynamoDB:
I hope that you find this powerful new access control feature to be of value. Leave me a comment and let me know what you think!
— Jeff;
相關推薦
Fine-Grained Access Control for Amazon DynamoDB
I truly enjoy the process of putting blog posts together for new AWS services and features. Many features started out as specific requests from on
Fine Grained Access Control in Cloudera Manager
One instance of Cloudera Manager (CM) can manage N clusters. In the current Role Based Access Control (RBAC) model, CM users hold privileges and perm
ORA-39181: Only partial table data may be exported due to fine grain access control on "OE"."PURCHAS
操作環境:Oracle Linux 6.5+Oracle11g 今天在用資料泵匯出表空間的實驗中出現一個錯誤:ORA-39181: Only partial table dat
全新推出 – Auto Scaling for Amazon DynamoDB
Amazon DynamoDB 擁有十萬多的客戶,客戶身處各種行業,使用案例也各不相同。這些客戶依賴於 DynamoDB 在任何規模下都能提供的一致性能和覆蓋全球 16 個地理區域的服務網路。最近我們注意到一個趨勢,客戶正在使用 DynamoDB 來為他們的無伺服器應用程式提供支援。這是一個
MACNN-Learning Multi-Attention Convolutional Neural Network for Fine-Grained Image Recognition
《Learning Multi-Attention Convolutional Neural Network for Fine-Grained Image Recognition》是微軟亞洲研究院17年出的一篇細粒度影象識別論文,它的姊妹篇是《Look Closer to
Two-level attention model for fine-grained Image classification
The Application of Two-level Attention Models in Deep Convolutional Neural Network for Fine-grained Image Classification(細粒度影象識別) 原文連結:
Pairwise Confusion for Fine-Grained Visual Classification 閱讀筆記
1) 摘要 儘管細粒度視覺分類資料集的樣本數量很少,但是卻存在著顯著的類內差異性和類別間相似性。然而,先前的工作通常採用定位或者分割來解決類內的差異性,但是,類別間相似性依然影響特徵的學習從而降低分類器的效能。針對這一問題,我們提出了一種可端到端驚醒訓練的新奇的優化方法--
論文筆記:雙線性模型 《Bilinear CNN Models for Fine-Grained Visual Recognition》
雙線性模型是2015年提出的一種細粒度影象分類模型。該模型使用的是兩個並列的CNN模型,這種CNN模型使用的是AlexNet或VGGNet去掉最後的全連線層和softmax層,這個作為特徵提取器,然後使用SVM作為最後的線性分類器。當然,作者還在實驗中嘗試了多種方法,比如最後使用softmax但
Lingke: A Fine-grained Multi-turn Chatbot for Customer Service
最近做問答系統領域,要求自己每天讀一篇論文,為幫助自己理解和記憶,將要點記錄在部落格上 摘要 機器人型別:資訊檢索型機器人(給一段資料回答問題) 特色功能:1)基於給定的產品說明書回答問題;2)能夠應對多輪對話 方案流程
Prepare Environment for Working with AWS CLI and Amazon DynamoDB on Amazon EC2
Amazon Web Services is Hiring. Amazon Web Services (AWS) is a dynamic, growing business unit within Amazon.com. We are currently hiring So
【轉載】細粒度影象識別Object-Part Attention Driven Discriminative Localization for Fine-grained Image Classification
細粒度影象識別Object-Part Attention Driven Discriminative Localization for Fine-grained Image Classification(OPADDL) 論文筆記 原文:"Object-Part Attention Model for Fin
Node.js使用MongoDB3.4+Access control is not enabled for the database解決方案
今天使用MongoDB時遇到了一些問題 建立資料庫連線時出現了warnings 出現這個警告的原因是新版本的MongDB為了讓我們建立一個安全的資料庫 必須要進行驗證 後來在外網找到了答案 解決方案如下: 建立管理員 use admin d
MYSQL: ERROR 1045 (28000): Access denied for user 'root'@'localhost' (using password: YES)
tar new ica host star init upd pass skip 1) /etc/init.d/mysqld stop2) mysqld_safe --skip-grant-tables &3) mysql -u root4) Setup new M
MySQL提示Access denied for user ''@'localhost'”的解決
bsp con sta class safe starting sin 改錯 pri 記得那時由於沒有網絡,把rootpassword改錯了寫成了: update user set password="122" where user="root"; 之後mysql就開始
ERROR 1044 (42000): Access denied for user ''@'localhost' to database 'mysql'
centos 解決 ice 個數 oca 用戶 acc 登錄 use 在centos下安裝好了mysql,用root帳號連上mysql,然後創建一個數據庫,提示下圖錯誤: 提示:ERROR 1044 (42000): Access denied for user [e
mariadb mysql 報'Access denied for user 'root'@'localhost' (using password: NO)'錯誤的解決
min other oca rac none mysql oot com command C:\Program Files\MariaDB 10.2\bin>mysql admin -u root password "x123456789" mysql Ver
Azure RBAC(Roles Based Access Control)正式上線了
如果 ext 授權 開發 fonts style clas 應用程序 tex 期盼已久的Azure RBAC(Roles Based Access Control)正式上線了。在非常多情況下。客戶須要對各種類型的用戶加以區分,以便做出適當的授權決定。基於角色的訪問控制
Access denied for user 'Administrator'@'localhost' (using password: YES)
pro 方式 chan bsp user mini hold 文件中 rri 在Spring容器中通過配置 <context:property-placeholder location="classpath:/jdbc.properties"/> 調用prope
No 'Access-Control-Allow-Origin' header is present on the requested resource
請求 ted -c ref aliyun 跨域 sent res 服務器的響應 一、現象 ajax調用請求後,前端提示收到這個錯誤 No ‘Access-Control-Allow-Origin‘ header is present on the requested res
ERROR 1045 (28000): Access denied for user 'root'@'localhost' (using password: YES)
註釋 .cn tables table 數據 mysql數據庫 using ice 登錄 解決: (1)修改my.cnf中[mysqld]中增加skip-grant-tables (2)重啟mysql數據庫:service mysqld restart (3)無密碼登錄my
