路由器逆向分析------binwalk工具的安裝
一、binwalk工具執行支援的平臺
| Operating System | Core Support | Optional Feature Support | Ease of Installation |
|---|---|---|---|
| Linux | Excellent | Excellent | Very easy |
| OSX | Excellent | Good | Very easy |
| FreeBSD | Experimental | Unknown | Very easy |
| Windows | Experimental | Poor | Very easy |
在Linux下使用binwalk工具效果最佳,坑最少;推薦在ubuntu系統下安裝和使用binwalk工具。
二、binwalk工具的簡單安裝
Installation
Binwalk follows the standard Python installation procedure:
$ sudo python setup.py install
If you're running Python 2.x, you'll also want to install the Python lzma module:
$ sudo apt-get install python-lzma在binwalk工具的簡單安裝之前,需要在ubuntu系統上安裝好python,binwalk工具簡單安裝的命令過程如下:
binwalk工具的詳細使用幫助說明:$ sudo apt-get update $ sudo apt-get install build-essential autoconf git $ git clone https://github.com/devttys0/binwalk $ cd binwalk $ sudo python setup.py install # 如果安裝的是 python 2.x,還需要安裝python-lzma模組 $ sudo apt-get install python-lzma
binwalk的簡單安裝功能有限,只能將對裝置的韌體進行檔案組成格式的分析和裝置的檔案系統進行提取,不能對提取後的裝置檔案系統進行解壓處理。要binwalk工具能對提取後的裝置檔案系統進行解壓還需要安裝binwalk工具需要的依賴庫和元件工具。Binwalk v2.1.2b Craig Heffner, http://www.binwalk.org Usage: binwalk [OPTIONS] [FILE1] [FILE2] [FILE3] ... Disassembly Scan Options: -Y, --disasm Identify the CPU architecture of a file using the capstone disassembler -T, --minsn=<int> Minimum number of consecutive instructions to be considered valid (default: 500) -k, --continue Don't stop at the first match Signature Scan Options: -B, --signature Scan target file(s) for common file signatures -R, --raw=<str> Scan target file(s) for the specified sequence of bytes -A, --opcodes Scan target file(s) for common executable opcode signatures -m, --magic=<file> Specify a custom magic file to use -b, --dumb Disable smart signature keywords -I, --invalid Show results marked as invalid -x, --exclude=<str> Exclude results that match <str> -y, --include=<str> Only show results that match <str> Extraction Options: -e, --extract Automatically extract known file types -D, --dd=<type:ext:cmd> Extract <type> signatures, give the files an extension of <ext>, and execute <cmd> -M, --matryoshka Recursively scan extracted files -d, --depth=<int> Limit matryoshka recursion depth (default: 8 levels deep) -C, --directory=<str> Extract files/folders to a custom directory (default: current working directory) -j, --size=<int> Limit the size of each extracted file -n, --count=<int> Limit the number of extracted files -r, --rm Delete carved files after extraction -z, --carve Carve data from files, but don't execute extraction utilities Entropy Analysis Options: -E, --entropy Calculate file entropy -F, --fast Use faster, but less detailed, entropy analysis -J, --save Save plot as a PNG -Q, --nlegend Omit the legend from the entropy plot graph -N, --nplot Do not generate an entropy plot graph -H, --high=<float> Set the rising edge entropy trigger threshold (default: 0.95) -L, --low=<float> Set the falling edge entropy trigger threshold (default: 0.85) Raw Compression Options: -X, --deflate Scan for raw deflate compression streams -Z, --lzma Scan for raw LZMA compression streams -P, --partial Perform a superficial, but faster, scan -S, --stop Stop after the first result Binary Diffing Options: -W, --hexdump Perform a hexdump / diff of a file or files -G, --green Only show lines containing bytes that are the same among all files -i, --red Only show lines containing bytes that are different among all files -U, --blue Only show lines containing bytes that are different among some files -w, --terse Diff all files, but only display a hex dump of the first file General Options: -l, --length=<int> Number of bytes to scan -o, --offset=<int> Start scan at this file offset -O, --base=<int> Add a base address to all printed offsets -K, --block=<int> Set file block size -g, --swap=<int> Reverse every n bytes before scanning -f, --log=<file> Log results to file -c, --csv Log results to file in CSV format -t, --term Format output to fit the terminal window -q, --quiet Suppress output to stdout -v, --verbose Enable verbose output -h, --help Show help output -a, --finclude=<str> Only scan files whose names match this regex -p, --fexclude=<str> Do not scan files whose names match this regex -s, --status=<int> Enable the status server on the specified port
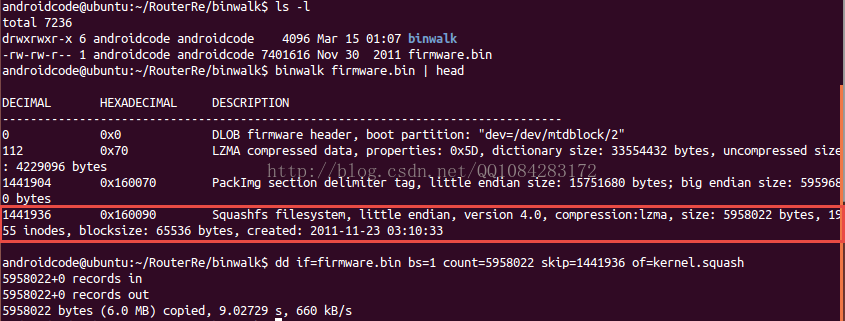
使用binwalk工具對裝置的韌體進行檔案組成格式的分析(以路由器韌體的分析為例):
$ binwalk firmware.bin | head使用binwalk工具對裝置的韌體檔案系統進行提取(以路由器韌體的分析為例):
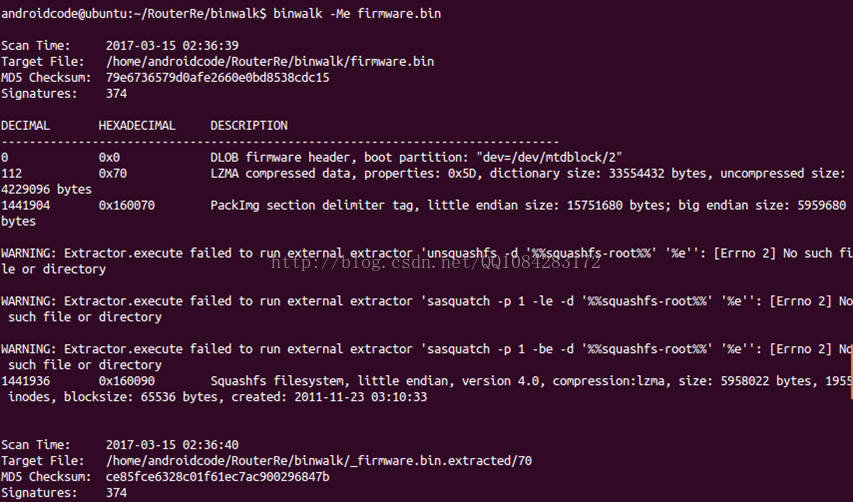
$ binwalk -e firmware.bin
# 或者
$ binwalk -Me firmware.bin檔案系統的提取結果如圖:
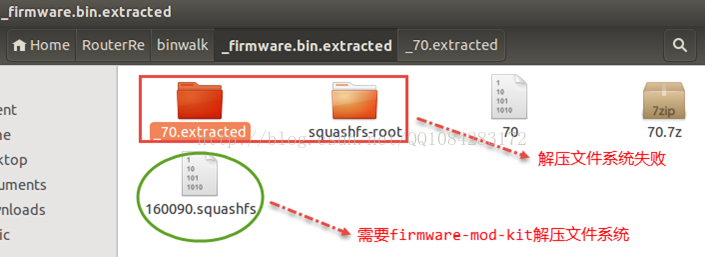
從上面的提取結果來看,binwalk雖然對路由器韌體的檔案系統squashfs提取成功,但是檔案系統squashfs解壓卻失敗,主要的原因是因為binwalk工具的安裝不完整,後面會提到binwalk工具的完整安裝。
當然了,binwalk還有一種更簡單的直接安裝方式:
$ sudo apt-get update
$ sudo apt-get install binwalk三、binwalk工具的完整安裝
Before You Start
Binwalk supports Python 2.7 - 3.x. Although most systems have Python2.7 set as their default Python interpreter, binwalk does run faster in Python3. Installation procedures for both are provided below.
Installation
Installation follows the typical Python installation procedure:
# Python2.7
$ sudo python setup.py install
# Python3.x
$ sudo python3 setup.py install
NOTE: Older versions of binwalk (e.g., v1.0) are not compatible with the latest version of binwalk. It is strongly recommended that you uninstall any existing binwalk installations before installing the latest version in order to avoid API conflicts.
Dependencies
Besides a Python interpreter, there are no installation dependencies for binwalk. All dependencies are optional run-time dependencies, and unless otherwise specified, are available from most Linux package managers.
Although all binwalk run-time dependencies are optional, the python-lzma module is highly recommended for improving the reliability of signature scans.
This module is included by default in Python3, but must be installed separately for Python2.7:
$ sudo apt-get install python-lzma
Binwalk uses the pycrypto library to decrypt some known encrypted firmware images:
# Python2.7
$ sudo apt-get install python-crypto
# Python3.x
$ sudo apt-get install python3-crypto
Binwalk uses pyqtgraph to generate graphs and visualizations, which requires the following:
# Python2.7
$ sudo apt-get install libqt4-opengl python-opengl python-qt4 python-qt4-gl python-numpy python-scipy python-pip
$ sudo pip install pyqtgraph
# Python3.x
$ sudo apt-get install libqt4-opengl python3-opengl python3-pyqt4 python3-pyqt4.qtopengl python3-numpy python3-scipy python3-pip
$ sudo pip3 install pyqtgraph
Binwalk's --disasm option requires the Capstone disassembly
framework and its corresponding Python bindings:
# Python2.7
$ sudo apt-get install python-pip
$ sudo pip install capstone
# Python3.x
$ sudo apt-get install python3-pip
$ sudo pip3 install capstone
Binwalk relies on multiple external utilties in order to automatically extract/decompress files and data:
# Install standard extraction utilities
$ sudo apt-get install mtd-utils gzip bzip2 tar arj lhasa p7zip p7zip-full cabextract cramfsprogs cramfsswap squashfs-tools
# Install sasquatch to extract non-standard SquashFS images $ sudo apt-get install zlib1g-dev liblzma-dev liblzo2-dev $ git clone https://github.com/devttys0/sasquatch $ (cd sasquatch && ./build.sh)
# Install jefferson to extract JFFS2 file systems $ sudo pip install cstruct $ git clone https://github.com/sviehb/jefferson $ (cd jefferson && sudo python setup.py install)
# Install ubi_reader to extract UBIFS file systems $ sudo apt-get install liblzo2-dev python-lzo $ git clone https://github.com/jrspruitt/ubi_reader $ (cd ubi_reader && sudo python setup.py install)
# Install yaffshiv to extract YAFFS file systems $ git clone https://github.com/devttys0/yaffshiv $ (cd yaffshiv && sudo python setup.py install)
# Install unstuff (closed source) to extract StuffIt archive files $ wget -O - http://my.smithmicro.com/downloads/files/stuffit520.611linux-i386.tar.gz | tar -zxv $ sudo cp bin/unstuff /usr/local/bin/
Note that for Debian/Ubuntu users, all of the above dependencies can be installed automatically using the included deps.shscript:
$ sudo ./deps.sh
Quick Start Guide
Peter Wu edited this page on 21 May 2016 · 14 revisionsInstallation
Download binwalk:
$ wget https://github.com/devttys0/binwalk/archive/master.zip $ unzip master.zip
Install binwalk; if you have a previously installed version of binwalk, it is suggested that you uninstall it before upgrading:
$ (cd binwalk-master && sudo python setup.py uninstall && sudo python setup.py install)
Debian users can install all optional and suggested extractors/dependencies using the includeddeps.sh script
(recommended):
$ sudo ./binwalk-master/deps.sh
If you are not a Debian user, or if you wish to install only selected dependencies, see the INSTALLdocumentation for more details.
Scanning Firmware
The primary - and by far the most popular - feature of binwalk is its signature scanning.
Binwalk can scan a firmware image for many different embedded file types and file systems; just give it a list of files to scan:
$ binwalk firmware.bin DECIMAL HEX DESCRIPTION ------------------------------------------------------------------------------------------------------------------- 0 0x0 DLOB firmware header, boot partition: "dev=/dev/mtdblock/2" 112 0x70 LZMA compressed data, properties: 0x5D, dictionary size: 33554432 bytes, uncompressed size: 3797616 bytes 1310832 0x140070 PackImg section delimiter tag, little endian size: 13644032 bytes; big endian size: 3264512 bytes 1310864 0x140090 Squashfs filesystem, little endian, version 4.0, compression:lzma, size: 3264162 bytes, 1866 inodes, blocksize: 65536 bytes, created: Tue Apr 3 04:12:22 2012
File Extraction
You can tell binwalk to extract any files that it finds in the firmware image with the -e option:
$ binwalk -e firmware.bin
Binwalk will even recursively scan files as it extracts them if you also specify the -M option:
$ binwalk -Me firmware.bin
And if the -r option is specified, any file signatures that couldn't be extracted - or that resulted
in 0-size files - will be automatically deleted:
$ binwalk -Mre firmware.bin
To extract one specific signature type, specify one or more -D type options:
$ binwalk -D 'png image:png' firmware.bin
Entropy Analysis
What happens if binwalk doesn't report any signatures? Or, how do you know binwalk didn't miss anything interesting?
Entropy analysis can help identify interesting sections of data inside a firmware image:
$ binwalk -E firmware.bin
HINT: You can combine other scans with the entropy scan. For example, you can combine a signature scan with an entropy scan:
$ binwalk -B -E firmware.bin DECIMAL HEX DESCRIPTION ------------------------------------------------------------------------------------------------------------------- 36625 0x8F11 Zlib header, default compression
binwalk工具完整安裝方式的整理,以python 2.7的安裝為例,python 3.x的安裝類似。
1.最懶的方式,自動安裝依賴庫和元件工具。
$ sudo apt-get update
$ sudo apt-get install build-essential autoconf git
$ git clone https://github.com/devttys0/binwalk.git
$ cd binwalk
# python2.7安裝
$ sudo python setup.py install
# 自動安裝依賴庫檔案
$ sudo ./deps.sh2.快速安裝方式,自動安裝依賴庫和元件工具。
$ sudo apt-get update
$ sudo apt-get install build-essential autoconf git
# https://github.com/devttys0/binwalk/wiki/Quick-Start-Guide
$ wget https://github.com/devttys0/binwalk/archive/master.zip
$ unzip master.zip
$ (cd binwalk-master && sudo python setup.py uninstall && sudo python setup.py install)
# 自動安裝依賴庫檔案和工具元件
$ sudo ./binwalk-master/deps.sh3.有選擇性的安裝binwalk的依賴庫檔案和元件工具。
$ sudo apt-get update
$ sudo apt-get install build-essential autoconf git
# https://github.com/devttys0/binwalk/blob/master/INSTALL.md
$ git clone https://github.com/devttys0/binwalk.git
$ cd binwalk
# python2.7安裝
$ sudo python setup.py install
# python2.7手動安裝依賴庫
$ sudo apt-get install python-lzma
$ sudo apt-get install python-crypto
$ sudo apt-get install libqt4-opengl python-opengl python-qt4 python-qt4-gl python-numpy python-scipy python-pip
$ sudo pip install pyqtgraph
$ sudo apt-get install python-pip
$ sudo pip install capstone
# Install standard extraction utilities(必選)
$ sudo apt-get install mtd-utils gzip bzip2 tar arj lhasa p7zip p7zip-full cabextract cramfsprogs cramfsswap squashfs-tools
# Install sasquatch to extract non-standard SquashFS images(必選)
$ sudo apt-get install zlib1g-dev liblzma-dev liblzo2-dev
$ git clone https://github.com/devttys0/sasquatch
$ (cd sasquatch && ./build.sh)
# Install jefferson to extract JFFS2 file systems(可選)
$ sudo pip install cstruct
$ git clone https://github.com/sviehb/jefferson
$ (cd jefferson && sudo python setup.py install)
# Install ubi_reader to extract UBIFS file systems(可選)
$ sudo apt-get install liblzo2-dev python-lzo
$ git clone https://github.com/jrspruitt/ubi_reader
$ (cd ubi_reader && sudo python setup.py install)
# Install yaffshiv to extract YAFFS file systems(可選)
$ git clone https://github.com/devttys0/yaffshiv
$ (cd yaffshiv && sudo python setup.py install)
# Install unstuff (closed source) to extract StuffIt archive files(可選)
$ wget -O - http://my.smithmicro.com/downloads/files/stuffit520.611linux-i386.tar.gz | tar -zxv
$ sudo cp bin/unstuff /usr/local/bin/Installing the IDA Plugin
If IDA is installed on your system, you may optionally install the binwalk IDA plugin:
$ python setup.py idainstall --idadir=/home/user/ida
Likewise, the binwalk IDA plugin can be uninstalled:
$ python setup.py idauninstall --idadir=/home/user/ida
Usage
Once installed, there will be two new menu options in IDA's Search drop-down menu list:
- binwalk signatures - Scans the loaded IDB for file signatures
- binwalk opcodes - Scans the loaded IDB for common opcode signatures
Results are printed to IDA's output window:
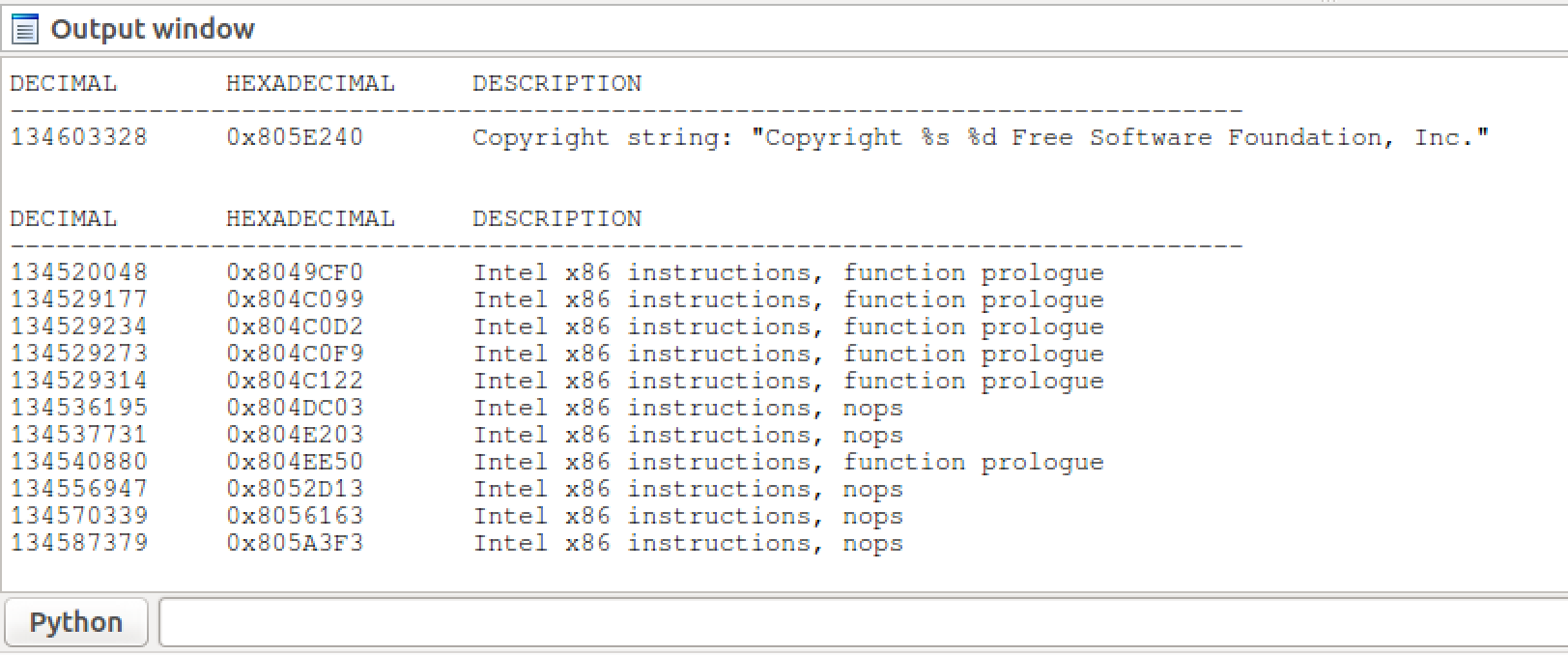
五、binwalk工具的解除安裝
Uninstalling Binwalk
If binwalk has been installed to a standard system location (e.g., via setup.py install), it can be removed by running:
# Python2.7
$ sudo python setup.py uninstall
# Python3
$ sudo python3 setup.py uninstall
Note that this does not remove any of the manually installed dependencies.