MacOS微信逆向分析-Frida
阿新 • • 發佈:2021-02-16
## MacOS微信逆向分析-Frida
### 0.前言
------
PC下的微信二次開發相信大家都會了,那麼本篇文章將帶領大家使用Frida框架對Mac下微信來進行**二次開發**!
PS:還有一種靜態注入的方式也不錯,但是考慮到大家xcode安裝包太大就不在這裡展開啦。
PS:frida如何去使用大家得自己去學,本文不過多展開。
主要功能涉及如下:
1. 微信訊息傳送
2. 微信訊息監聽
### 1.微信版本
------
### 2.工具
------
預先善其事,必先利其器!請先準備如下分析工具
1. [*Hopper* Disassembler](https://www.hopperapp.com/)
2. [Class-dump](http://stevenygard.com/projects/class-dump/)
3. [Frida](https://frida.re/)
4. [Pycharm](https://www.jetbrains.com/)(可選)
5. [Vscode](https://code.visualstudio.com/)(可選)
### 3.**Dump 出頭檔案**
------
首先利用Class-Dump拿到微信的標頭檔案,開啟終端執行:
```shell
class-dump -H /Applications/WeChat.app
```
成功執行之後會生成很多的標頭檔案了,如下所示
```shell
-rw-r--r-- 1 n staff 927B 2 15 19:19 WXCPbQcwxtalkPackage.h
-rw-r--r-- 1 n staff 975B 2 15 19:19 WXCPbReportItem.h
-rw-r--r-- 1 n staff 1.7K 2 15 19:19 WXCPbSCAddVoiceGroupMemberResp.h
-rw-r--r-- 1 n staff 772B 2 15 19:19 WXCPbSCCancelCreateVoiceGroupResp.h
-rw-r--r-- 1 n staff 7.2K 2 15 19:19 WXCPbSCCreateVoiceGroupResp.h
-rw-r--r-- 1 n staff 6.9K 2 15 19:19 WXCPbSCEnterVoiceRoomResp.h
-rw-r--r-- 1 n staff 1.1K 2 15 19:19 WXCPbSCExitVoiceRoomResp.h
-rw-r--r-- 1 n staff 1.2K 2 15 19:19 WXCPbSCModifyVoiceGroupInfoResp.h
-rw-r--r-- 1 n staff 872B 2 15 19:19 WXCPbSCSubscribeLargeVideoResp.h
-rw-r--r-- 1 n staff 867B 2 15 19:19 WXCPbSCSubscribeVideoResp.h
-rw-r--r-- 1 n staff 2.0K 2 15 19:19 WXCPbSCVoiceClientSceneReportResp.h
-rw-r--r-- 1 n staff 864B 2 15 19:19 WXCPbSCVoiceGetGroupInfoBatchResp.h
-rw-r--r-- 1 n staff 637B 2 15 19:19 WXCPbSCVoiceMemberWhisperResp.h
-rw-r--r-- 1 n staff 5.9K 2 15 19:19 WXCPbSCVoiceRedirectResp.h
-rw-r--r-- 1 n staff 1.1K 2 15 19:19 WXCPbSCVoiceRoomHelloResp.h
-rw-r--r-- 1 n staff 904B 2 15 19:19 WXCPbSKBuiltinBuffer_t.h
-rw-r--r-- 1 n staff 686B 2 15 19:19 WXCPbSubscribeVideoMember.h
-rw-r--r-- 1 n staff 2.7K 2 15 19:19 WXCPbSwitchVideoGroupResp.h
-rw-r--r-- 1 n staff 1.4K 2 15 19:19 WXCPbVideoGroupMember.h
-rw-r--r-- 1 n staff 671B 2 15 19:19 WXCPbVoiceClientScene.h
-rw-r--r-- 1 n staff 1.2K 2 15 19:19 WXCPbVoiceClientSceneExt.h
-rw-r--r-- 1 n staff 2.9K 2 15 19:19 WXCPbVoiceConf.h
```
### 4.分析
------
首先那麼多的檔案我們肯定不能一個個的去看,那樣效率太低。相信大家做開發為了自己好維護程式碼,肯定不會給物件隨便命名為abc這種吧!不會吧!不會吧!真的有這種人啊!!!但是我相信騰訊的程式設計師肯定不會這麼做!!微信核心的功能是啥?是發訊息哦,那麼訊息的英文是啥?**Message** !對就是他。所以我們就先塞選下這個**Message**!
```shell
# n @ localhost in ~/vscodewsp/wechat/dump [20:58:22]
$ ll |wc -l
4922
# n @ localhost in ~/vscodewsp/wechat/dump [20:58:29]
$ ll -l |grep Message|wc -l
157
# n @ localhost in ~/vscodewsp/wechat/dump [20:58:42]
```
執行如上命令我們把檔案數從4922個轉變到157了。這樣就縮小了範圍啦!如何再次縮小範圍尼!那麼就得是看大家的開發習慣啦,我一般做業務我都喜歡寫service,controller,這種業務類名,於是我再次....
```shell
# n @ localhost in ~/vscodewsp/wechat/dump [20:58:42]
$ ll -l |grep Message|grep Service|wc -l
9
# n @ localhost in ~/vscodewsp/wechat/dump [21:02:13]
$ ll -l |grep Message|grep Service
-rw-r--r-- 1 n staff 5.1K 2 15 19:19 FTSFileMessageService.h
-rw-r--r-- 1 n staff 382B 2 15 19:19 IMessageServiceAppExt-Protocol.h
-rw-r--r-- 1 n staff 980B 2 15 19:19 IMessageServiceFileExt-Protocol.h
-rw-r--r-- 1 n staff 381B 2 15 19:19 IMessageServiceFileReTransferExt-Protocol.h
-rw-r--r-- 1 n staff 755B 2 15 19:19 IMessageServiceImageExt-Protocol.h
-rw-r--r-- 1 n staff 780B 2 15 19:19 IMessageServiceVideoExt-Protocol.h
-rw-r--r-- 1 n staff 407B 2 15 19:19 IMessageServiceVideoReTransferExt-Protocol.h
-rw-r--r-- 1 n staff 3.1K 2 15 19:19 MMFTSMessageService.h
-rw-r--r-- 1 n staff 20K 2 15 19:19 MessageService.h
# n @ localhost in ~/vscodewsp/wechat/dump [21:02:25]
$
```
哎呦哎呦,就剩9個檔案啦???那麼這個一個個看也不礙事!!有時間就是任性!!!哼。最終定位到**MessageService.h** 開啟一看,果然尼!真是運氣好!
```swift
- (id)SendLocationMsgFromUser:(id)arg1 toUser:(id)arg2 withLatitude:(double)arg3 longitude:(double)arg4 poiName:(id)arg5 label:(id)arg6;
- (id)SendNamecardMsgFromUser:(id)arg1 toUser:(id)arg2 containingContact:(id)arg3;
- (id)SendStickerStoreEmoticonMsgFromUsr:(id)arg1 toUsrName:(id)arg2 md5:(id)arg3 productID:(id)arg4;
- (id)SendEmoticonMsgFromUsr:(id)arg1 toUsrName:(id)arg2 md5:(id)arg3 emoticonType:(unsigned int)arg4;
- (id)SendImgMessage:(id)arg1 toUsrName:(id)arg2 thumbImgData:(id)arg3 midImgData:(id)arg4 imgData:(id)arg5 imgInfo:(id)arg6;
- (id)SendTextMessage:(id)arg1 toUsrName:(id)arg2 msgText:(id)arg3 atUserList:(id)arg4;
- (id)SendAppMusicMessageFromUser:(id)arg1 toUsrName:(id)arg2 withTitle:(id)arg3 url:(id)arg4 description:(id)arg5 thumbnailData:(id)arg6;
- (id)SendAppURLMessageFromUser:(id)arg1 toUsrName:(id)arg2 withTitle:(id)arg3 url:(id)arg4 description:(id)arg5 thumbnailData:(id)arg6;
- (id)SendAppURLMessageFromUser:(id)arg1 toUsrName:(id)arg2 withTitle:(id)arg3 url:(id)arg4 description:(id)arg5 thumbUrl:(id)arg6 sourceUserName:(id)arg7 sourceDisplayName:(id)arg8;
```
你看這功能不就來了嘛?Send開頭的都是傳送訊息的函式啊。OK完事。那麼就開始搞它!
PS:其實分析時候還是挺費事的,但是大家自己多動手肯定能找到的!
### 5.FridaHook驗證
------
為了驗證自己的分析是不是正確的,我們得進行驗證啊,怎麼驗證?frida大法好!執行以下命令:
`frida-trace -m "-[MessageService Send*]" 微信`
```shell
$ frida-trace -m "-[MessageService Send*]" 微信
Instrumenting...
-[MessageService SendTextMessageWithString:toUser:]: Auto-generated handler at "/Users/n/vscodewsp/wechat/__handlers__/MessageService/SendTextMessageWithString_toUser_.js"
-[MessageService SendAppURLMessageFromUser:toUsrName:withTitle:url:description:thumbUrl:sourceUserName:sourceDisplayName:]: Auto-generated handler at "/Users/n/vscodewsp/wechat/__handlers__/MessageService/SendAppURLMessageFromUser_toUsrN_eaefd0af.js"
------------------------------------------------------------------------------
-[MessageService SendNamecardMsgFromUser:toUser:containingContact:]: Auto-generated handler at "/Users/n/vscodewsp/wechat/__handlers__/MessageService/SendNamecardMsgFromUser_toUser_c_b5899e8d.js"
Started tracing 18 functions. Press Ctrl+C to stop.
```
然後會在當前目錄生成__handlers__資料夾,裡面是frida為我們自動生成的hook指令碼檔案。我們使用微信傳送一條訊息試試。
然後終端會輸出一條資訊:
`195323 ms -[MessageService SendTextMessage:0x600000b6fae0 toUsrName:0x6503cfa934d442eb msgText:0x6000002ec860 atUserList:0x600000a73570]`
這個就是觸發了傳送訊息的hook資訊啦。**SendTextMessage** 是不是跟我們在標頭檔案資訊裡面看到的一樣。
我們找到handles資料夾下**SendTextMessage**這個js檔案,試試修改log輸出然後再執行
`frida-trace -m "-[MessageService Send*]" 微信`
我們可以看到輸出變啦
`2908 ms -[我的訊息測試 SendTextMessage:0x600000b6fae0 toUsrName:0x6503cfa934d442eb msgText:0x6722df8306c2767b atUserList:0x6000009c2760]`
如此可以確定我們找到的函式就是傳送訊息的函式。那麼看看能不能打印出自己傳送的訊息內容
`- (id)SendTextMessage:(id)arg1 toUsrName:(id)arg2 msgText:(id)arg3 atUserList:(id)arg4;`
可以看到這個函式一共有4個引數:引數一:暫時不知道。引數二:toUsrName,我們可以知道是訊息傳送給誰的。引數三:msgText 訊息內容,訊息四:暫時不知道
分別把這四個引數給打印出來試試!修改js檔案
```javascript
onEnter(log, args, state) {
console.log(`-[我的訊息測試 SendTextMessage:${args[2]} toUsrName:${args[3]} msgText:${args[4]} atUserList:${args[5]}]`);
console.log("arg[1] -> " + new ObjC.Object(args[2]))
console.log("arg[2] -> " + new ObjC.Object(args[3]))
console.log("arg[3] -> " + new ObjC.Object(args[4]))
console.log("arg[4] -> " + new ObjC.Object(args[5]))
},
```
然後執行 `frida-trace -m "-[MessageService Send*]" 微信` 傳送一條訊息
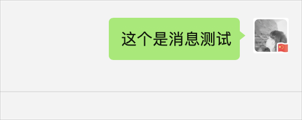 ```shell
arg[1] -> wxid_*****63i822
arg[2] ->
```shell
arg[1] -> wxid_*****63i822
arg[2] -> 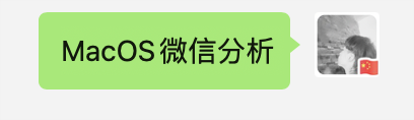
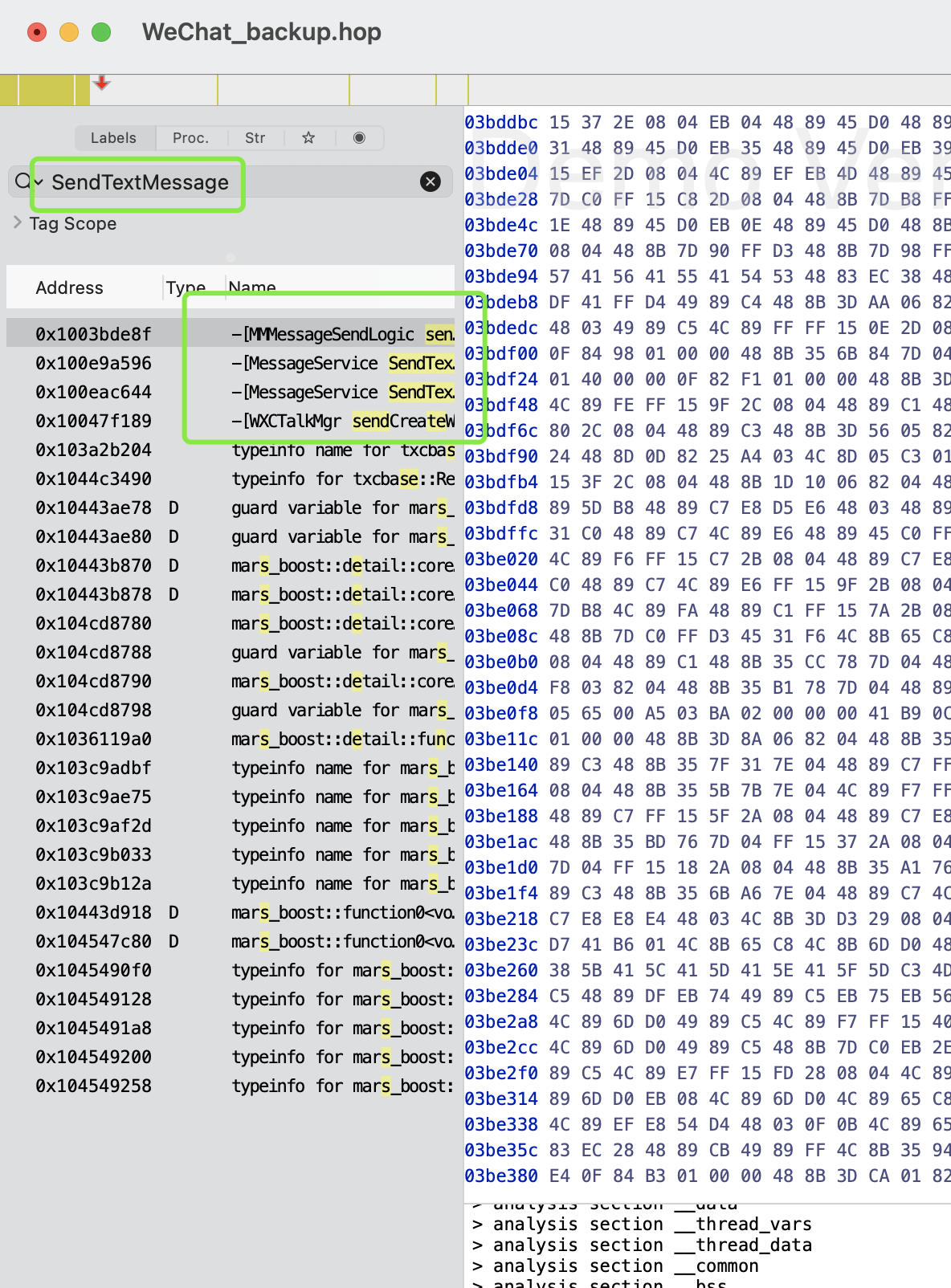 在左邊輸入**SendTextMessage**搜尋我們可以看到上面四個應該是我們所需要的,都開啟看下虛擬碼。(我們分析需要找到函式呼叫的地方就能知道傳參,然後再去分析引數是如何而來。那麼除了函式定義地方程式碼,其餘的都可以找到。
**MMMessageSendLogic** :
```swift
/* @class MMMessageSendLogic */
-(unsigned char)sendTextMessageWithString:(void *)arg2 mentionedUsers:(void *)arg3 {
r14 = self;
r15 = [arg2 retain];
r12 = [arg3 retain];
r13 = [[CUtility filterStringForTextMessage:r15] retain];
[r15 release];
if ([r13 length] != 0x0) {
stack[-64] = r12;
rax = [r13 lengthOfBytesUsingEncoding:0x4];
rbx = rax;
if (rax >
在左邊輸入**SendTextMessage**搜尋我們可以看到上面四個應該是我們所需要的,都開啟看下虛擬碼。(我們分析需要找到函式呼叫的地方就能知道傳參,然後再去分析引數是如何而來。那麼除了函式定義地方程式碼,其餘的都可以找到。
**MMMessageSendLogic** :
```swift
/* @class MMMessageSendLogic */
-(unsigned char)sendTextMessageWithString:(void *)arg2 mentionedUsers:(void *)arg3 {
r14 = self;
r15 = [arg2 retain];
r12 = [arg3 retain];
r13 = [[CUtility filterStringForTextMessage:r15] retain];
[r15 release];
if ([r13 length] != 0x0) {
stack[-64] = r12;
rax = [r13 lengthOfBytesUsingEncoding:0x4];
rbx = rax;
if (rax >
 ```shell
arg[1] -> wxid_*****63i822
arg[2] ->
```shell
arg[1] -> wxid_*****63i822
arg[2] ->
 在左邊輸入**SendTextMessage**搜尋我們可以看到上面四個應該是我們所需要的,都開啟看下虛擬碼。(我們分析需要找到函式呼叫的地方就能知道傳參,然後再去分析引數是如何而來。那麼除了函式定義地方程式碼,其餘的都可以找到。
**MMMessageSendLogic** :
```swift
/* @class MMMessageSendLogic */
-(unsigned char)sendTextMessageWithString:(void *)arg2 mentionedUsers:(void *)arg3 {
r14 = self;
r15 = [arg2 retain];
r12 = [arg3 retain];
r13 = [[CUtility filterStringForTextMessage:r15] retain];
[r15 release];
if ([r13 length] != 0x0) {
stack[-64] = r12;
rax = [r13 lengthOfBytesUsingEncoding:0x4];
rbx = rax;
if (rax >
在左邊輸入**SendTextMessage**搜尋我們可以看到上面四個應該是我們所需要的,都開啟看下虛擬碼。(我們分析需要找到函式呼叫的地方就能知道傳參,然後再去分析引數是如何而來。那麼除了函式定義地方程式碼,其餘的都可以找到。
**MMMessageSendLogic** :
```swift
/* @class MMMessageSendLogic */
-(unsigned char)sendTextMessageWithString:(void *)arg2 mentionedUsers:(void *)arg3 {
r14 = self;
r15 = [arg2 retain];
r12 = [arg3 retain];
r13 = [[CUtility filterStringForTextMessage:r15] retain];
[r15 release];
if ([r13 length] != 0x0) {
stack[-64] = r12;
rax = [r13 lengthOfBytesUsingEncoding:0x4];
rbx = rax;
if (rax >